Health and Social Care Act 2008 (Regulated Activities) Regulations 2014 [9, 10, 13]
Safeguarding
Involving people to manage risks
Safe and effective staffing
Assessing needs
Delivering evidence-based care and treatment
Supporting people to live healthier lives
Consent to care and treatment
Kindness, compassion and dignity
Treating people as individuals
Independence, choice and control
Person-centred care
Providing information
Listening to and involving people
Equity in access
Equity in experiences and outcomes
Planning for the future
Governance, management and sustainability
To ensure that service users, who may have communication needs relating to a disability, impairment or sensory loss, receive information in formats they are able to understand. This policy must be read and complied with by all managers and members of staff who are involved in providing care and supporting service users.
Our organisation is committed to equal rights and the promotion of choice, person-centred care and independence. This policy demonstrates our commitment to creating a positive culture of respect for all individuals. The intention is, as required by the Equality Act 2010, to identify, remove or minimise discriminatory practice in the nine named protected characteristics of age, disability, sex, gender reassignment, pregnancy and maternity, race, sexual orientation, religion or belief, and marriage and civil partnership. It is also intended to reect the Human Rights Act 1998 to promote positive practice and value the diversity of all individuals.
1. The Accessible Information Standard (AIS) became a legal requirement in August 2016 for all organisations that provide NHS care and/or publicly funded adult social care and was amended in 2017.
2. The aim of the AIS is to ensure people who have a disability, impairment or sensory loss are provided with information in a form that meets their communication needs.
3. Providing accessible information ensures service users who have a disability, impairment or sensory loss are provided with information in a form that meets their communication needs. This supports people to understand their options and make informed decisions about their care and support.
4. For each service user, the organisation will complete a full assessment of needs, including identifying any accessible information needs.
5. There are ve steps of AIS: identify, record, ag, share, and meet.
6. The care and support plan will identify the communication needs and solutions for the service user or their carer.
7. Staff must support the service user or their carer in meeting these needs.
8. Care and support reviews will include communication needs, and these will be updated as new solutions become available or the service user’s needs change.
The Accessible Information Standard (AIS) became a legal requirement in August 2016 for all organisations that provide NHS care and/or publicly funded adult social care.The guidelines were revised in 2017 and set out a consistent approach to ensure that the communication support needs of service users, carers and parents with a disability, impairment or sensory loss will be met by the organisation’s services.
The aim of the AIS is to establish a framework and set a clear direction so that service users who use these services, and, where appropriate, carers and parents, who have information or communication needs relating to a disability, impairment or sensory loss receive:
1. Accessible Information – information which can be read, or received, and understood by the individual, or group, for which it is intended, and
2. Communication support – support which is needed to enable effective, accurate dialogue between a professional and a service user to take place.
This is to prevent individuals being at a substantial disadvantage when accessing NHS or adult social services. This includes accessible information and communication support to enable individuals to:
1. Make decisions about their health and wellbeing, and about their care and treatment.
2. Self-manage conditions
3. Access services appropriately and independently
4. Make choices about treatments and procedures, including the provision or withholding of consent.
This policy outlines our commitment to ensure that all service users who use our services and their carers/families where required, will receive communication and information in an appropriate format to support their needs.
The AIS includes interpretation or translation for people whose rst language is British Sign Language. It does not cover these needs for other languages, which are covered under the Equality Act 2010.
The AIS is not a requirement for service users which are not publicly funded, however the organisation will take the same approach for privately funded service users in compliance with the Equality Act 2010.
The organisation will adopt a consistent approach to the identication of service users’, carers’ and parents’ information and communication needs, where they relate to a disability, impairment or sensory loss.
Information and communication needs related to disability, impairment and sensory loss will be identied at the care assessment and will include the service user, family and relevant circle of support, e.g. speech therapist, as appropriate. The assessment will include exploration and identication of solutions to meet the service user’s or the carer’s needs.
The organisation will:
1. Adopt a consistent and routine recording of service users’ and, where appropriate, carers’ and parents’ information and communication needs, where they relate to a disability, impairment or sensory loss, as part of service user records and administration systems,
2. Use specied English denitions indicating needs, and
3. Record needs in such a way that they are ‘highly visible.’
Any disability that affects communication will be identied, with mitigation and support included within the care and support plan. At care and support reviews, communication needs will be reviewed and opportunities for new techniques, activities and aids will be explored with a view to better meeting the needs of the service user or their carer.
Standard and recognised clinical and English terms will be used to record needs to ensure clear communication with other social and healthcare professionals.
The organisation will establish and use electronic ags or alerts, or paper-based equivalents, to indicate that a service user or carer has a recorded information and/or communication need, and prompt staff to take appropriate action and/or trigger auto-generation of information in an accessible format or other actions to meet their needs.
The care and support plan, and oce electronic records will clearly identify service user or carer communication needs and identied solutions.
Where IT systems allow auto generated communication will provide information, e.g. letters, rosters, care plans, service user guides in a format which meets the needs of the service user or carer.
Where IT systems cannot auto generate information in the required format, then the oce administration staff will be responsible for ensuring information is provided in a format or media to support the service user or carers needs.
The organisation will include data about service users or carers accessible information needs and/or communication support as part of existing data-sharing processes, and as a routine part of referral, discharge and handover processes.
All data sharing between health and social care professionals who are supporting the service user, or the carer, will include information regarding their communication needs and the solutions in place to support them. This will include hospital grab sheet, communication passports, care and support plan and written communication with GPs and other professionals.
Communication passports or similar documents will be readily available for each service user. These will support the service user and families when attending hospital or other care environments. Service users, their families and friends will be involved and agree what is recorded, why it is recorded, and for what purpose. Descriptions will be personalised, individual, current, and up to date.
All records will be clearly written and free of jargon, acronyms, and abbreviations.
The organisation will ensure that the service users, or their carers, receive information in an accessible format and relevant communication support to meet their needs.
The care and support plan, and oce electronic records, will clearly identify service user or carer communication needs and identied solutions.
Examples of how information and regular communication will be made available to meet service user or their carers needs include the following ways:
1. Sign language, if this is the normal means of communication
2. Easy read, large print, braille and audio, where appropriate.
3. Communication Passports.
4. Communication Cards
5. In accordance with The Accessible Information Standard (SCCI 1605 (Accessible Information)), people can be issued with a communication card that they can carry around and hand over as formal notication of their information and communication preferences.
6. Communication Technology
7. Devices and software applications, e.g. sophisticated voice replicating computer equipment.
8. Signposting to third sector organisations which support communication, e.g. 1Voice.
9. Sensory communication.
10. Service users living with dyslexia will be supported in accordance with their needs, e.g. aiding the completion of forms by writing down what the person tells them and reading it back to them to ensure it is correct.
11. Information for service users who have a visual impairment will be provided in the appropriate written form to aid their vision or provided in audio format or braille.
12. Service users with a learning disability will be supported using language and information that will be adapted according to their individual need, e.g. in an easy read format.
13. Service users who wish to use electronic forms of communication, using their own technology, will be supported to do so, e.g. through email, text messaging, video clips and or other technology which supports their communication.
14. Managers and employees will seek external guidance/expertise from other professional organisations to assist with communication needs. This may include help to lip read, British Sign Language interpreter, Makaton interpreter, or the local sensory support service. Contact details of these organisations will be kept in the person’s care file.
The above is provided for information and the organisation will work with each service user, their family and circle of support to nd the best solutions to meet their specic needs and communication requirements.
Accessible Information Standard, NHS (https://www.england.nhs.uk/ourwork/accessibleinfo/)
Communication Passports (https://www.communicationpassports.org.uk/Home/)
Communication Card, RNID (https://rnid.org.uk/get-involved/create-a-personalised-digital-communication-card/)1Voice Charity (https://www.1voice.info/)
Accessible Information Standard, Mencap (https://www.mencap.org.uk/accessible-information-standard)
Speech and language therapy, RCSLT (https://www.rcslt.org/speech-and-language-therapy/)
The Sequal Trust (https://www.thesequaltrust.org.uk/)
We work with people to understand what being safe means to them as well as with our partners on the best way to achieve this. We concentrate on improving people’s lives while protecting their right to live in safety, free from bullying, harassment, abuse, discrimination, avoidable harm and neglect. We make sure we share concerns quickly and appropriately.
We work with people to understand and manage risks by thinking holistically so that care meets their needs in a way that is safe and supportive and enables them to do the things that matter to them.
We make sure there are enough qualified, skilled and experienced people, who receive effective support, supervision and development. They work together effectively to provide safe care that meets people’s individual needs.
We maximise the effectiveness of people’s care and treatment by assessing and reviewing their health, care, well-being and communication needs with them.
We plan and deliver people’s care and treatment with them, including what is important and matters to them. We do this in line with legislation and current evidence-based good practice and standards.
We support people to manage their health and well-being so they can maximise their independence, choice and control. We support them to live healthier lives and where possible, reduce their future needs for care and support.
We tell people about their rights around consent and respect these when we deliver person-centred care and treatment.
We always treat people with kindness, empathy and compassion and we respect their privacy and dignity. We treat colleagues from other organisations with kindness and respect.
We treat people as individuals and make sure their care, support and treatment meets their needs and preferences. We take account of their strengths, abilities, aspirations, culture and unique backgrounds and protected characteristics.
We promote people’s independence, so they know their rights and have choice and control over their own care, treatment and well-being.
We make sure people are at the centre of their care and treatment choices and we decide, in partnership with them, how to respond to any relevant changes in their needs.
We provide appropriate, accurate and up-to-date information in formats that we tailor to individual needs.
We make it easy for people to share feedback and ideas or raise complaints about their care, treatment and support. We involve them in decisions about their care and tell them what’s changed as a result.
We make sure that everyone can access the care, support and treatment they need when they need it.
We actively seek out and listen to information about people who are most likely to experience inequality in experience or outcomes. We tailor the care, support and treatment in response to this.
We support people to plan for important life changes, so they can have enough time to make informed decisions about their future, including at the end of their life.
We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.


Advocacy is about supporting you to have your say about what happens in your life

You are helped with this by people called Advocates.
Their job is to listen to you

Advocates can sometimes be your family or a close friend, or an independent person.
They cannot be someone who gets paid to help you, like your support worker.

The following information in this booklet is about independent advocates. These are people who do not work for social services or the NHS. This means they can support you to have a say if you are not happy with your care.

Advocates will talk to you to find out what you want and how you feel.

Advocates will support you to know your rights.

They will ask you if you want their help.
It is OK to say Yes or No

Advocates will only talk to other people:
If you ask them to
If you or someone you know might get hurt
When the law says they must

Advocates will help you make decisions
And make sure that your opinions are heard

Advocates can help you to make decisions about:
1. Where you live
2. What support you have
3. What to do if you are unwell

Advocates are free
You will not pay any money to see them

Advocates can help you with:
1. Speaking up at your meeting
2. Getting the right support
3. Making a complaint

Different laws say you can have an advocate if certain things in your life are happening

An Advocate will help you to understand your rights

They can help you to find information to help you make choices

They can tell other people what you want to happen.

Advocates help you say what you think about your care or Treatment

They can help you to make your own decisions

The law says that an advocate will help you with certain things:

1. Assessments and reviews that are carried out by social services or the NHS

2. When there are safeguarding concerns

3. If you are moving to a new home

4. If you need to have a stay in hospital because of an illness or injury

5. If a doctor says you are mentally unwell and need to stay in hospital

There are different ways that you can speak to an advocate:

1. You can meet them in person
2. You can talk to them on the telephone
3. You can have a video conversation

Tell your social worker or support worker if you think you need an advocate

They will sort out an appointment for you

You can find out more about advocacy here
Someone to speak up for you (advocate) – NHS


We want to know if you are not happy about something so that we can try to make it better.

A complaint is when you tell us you are not happy about something. We will listen to what is wrong and try to make it better.
We are happy for you to complain. It helps us to get better at what we do.

You can tell us what you are unhappy about in any way that suits you.

You can talk to anyone you feel comfortable with. This may be the manager or someone else.

You can ring us on the telephone.

You can write us a letter.

You can send us an email.

Staff will always be polite and respectful. You should stay calm and be polite as well.

The manager may not be able to sort out the problem straight away. They may give you a leaflet to explain how they will try to make things better.

We may write you a letter or talk with you to explain what we will do next.

We will tell you how long it will take to give you an answer to your complaint.

We will also tell you what will happen after we have sent our letter to you.

If you are not happy with how we have tried to make things better, we can tell you who else you can talk to.

An advocate is someone who will support you to resolve a problem or make a decision.

If you need any help with making a complaint you can:
1. Ask a member of staff
2. Ask a family member or friend
3. Ask an independent advocate



Health and Social Care Act 2008 (Regulated Activities) Regulations 2014 [9,10,11,16,17]
Please see the ‘Quality Statements’ section for full guidance
This policy includes all staff and contractors who are bound by a legal duty of confidence to protect personal information (including Special Category Data as defined in General Data Protection Regulations (GDPR)) they may come into contact with during the course of their work. This means that staff are obliged to keep any Personal Identifiable Data (sometimes referred to as PID), strictly confidential, e.g. medical and employee records.
It should be noted that staff also come into contact with non-person identifiable information which should also be treated with the same degree of care. Some data may be confidential to the organisation, and this again must be treated in confidence, e.g. new marketing campaigns, financial information.
This policy and procedure are provided for the regulated activity of personal care.
Our organisation is committed to equal rights and the promotion of choice, person-centred care and independence. This policy demonstrates our commitment to creating a positive culture of respect for all individuals. The intention is, as required by the Equality Act 2010, to identify, remove or minimise discriminatory practice in the nine named protected characteristics of age, disability, sex, gender reassignment, pregnancy and maternity, race, sexual orientation, religion or belief, and marriage and civil partnership. It is also intended to reflect the Human Rights Act 1998 to promote positive practice and value the diversity of all individuals.
1. All staff/contractors are responsible for maintaining the confidentiality of information gained during their employment/involvement with the organisation and this extends after they have left the employ of the organisation.
2.Much of this information is highly personal and sensitive. We recognise that our service users have a right to privacy and dignity, and that this extends to our handling information about them in ways which cause as little as possible intrusion on those rights.
3. We will only break the rule of confidentiality in very extreme circumstances which justify our taking that action for the greater good of a person using the service or, exceptionally, others in accordance with the Data Protection Act 2018 Code of Practice.
4. The Data Protection Act lays various obligations on this organisation and similar organisations concerning the handling of the information we hold on individuals.
5. Staff must receive information, training and support to understand their role in maintaining confidentiality and data protection.
6. Records must be prepared, maintained and used in accordance with data protection legislation.
7.A clear desk policy is keeping personal information secure and restricted to the minimum number of viewers possible. When you leave your desk, you should ensure that any personal or confidential information is not left lying around, or accessible via an unlocked computer screen for others to see.
As an organisation we comply with The Data Protection Act 2018 (DPA) and GDPR concerning confidentiality within the organisation and the services it delivers. It is essential that all information we hold, about any of our service users using the service and staff, is not disclosed without their permission. This includes withholding information from families if the service user requests it.
In addition, the organisation is aware of its responsibility to share information fairly and proportionately in line with the Data Protection Act section 121. The organisation will share information where there is a need to protect, safeguard and support the health and well-being of the service user or carer, and where it would be more harmful not to share information.
All staff/contractors are responsible for maintaining the confidentiality of information gained during their employment and or involvement with the organisation and this extends after they have left the employ of the organisation.
Definition of Confidential Information
Confidential information can be anything that relates to service users, team members, their family or friends, or the business of the organisation, however stored. For example, information may be held on paper, USB pen, CD, computer file or printout, video, photograph or even heard by word of mouth. It includes information stored on portable devices such as laptops, palmtops, USB pens, mobile phones and digital cameras. It also includes any organisation confidential information such as the service business information.
It is the aim of the organisation to manage all confidential information about individuals who may meet the organisation during the delivery of its services in compliance with all relevant legislation and regulations.
The work of the organisation inevitably involves the need-to-know personal details about our service users and their families or carers. The information is required to provide safe, effective, caring, responsive and well-led care and support to the service users.
Much of this information is highly personal and sensitive. We recognise that our service users using the service have a right to privacy and dignity, and that this extends to our handling information with minimal intrusion and impact on the service user or their families.
We want our service users to feel at ease with the staff that care for them. An important element in that relationship is the sharing of information with staff, confident that it will be used with appropriate respect and only in relation to the care provided.
Information within the organisation about individual service users will only be shared and provided to those staff who need the information to be able to care and support them, provide management and administration functions in the delivery of the service and other relevant tasks to ensure their needs are being met.
The organisation will share information where there is a need to protect, safeguard and support the health and well-being of the service user or carer, and where it would be more harmful not to share information. Staff and the organisation will always work in the best interests of the service user and will share information in line with the DPA 2018 Code of Practice. Where a service user lacks capacity to consent to sharing information, staff will work in accordance with the Mental Capacity Act 2005 to ensure that any information shared is done so in the person’s best interests.
As part of the contract with the service user (self-funding service users), and a separate confidentiality agreement for local authority/health referrals, the organisation will agree where and how information can be shared and under which circumstances. Examples of people information may be shared with include:
1. Their GP or other health care professionals treating the service user
2. Their Care Manager/Social Worker
3. Social care colleagues who are also working with this person using the service
4. Other care providers jointly providing services
5. Office staff and managers
6. CQC inspectors
7. Local authority/health commissioners
Examples of people you may not share information or discuss the service user with include your family and friends and your colleagues not involved in the service users’ care.
The DPA 2018 lays various obligations on this organisation and similar organisations concerning the handling of the information we hold on individuals. Information must, for example, be obtained fairly and lawfully, be held for specified purposes, be adequate, relevant and not excessive for the purpose for which it was gathered, be accurate and up to date, and not be held for longer than is necessary. We observe all of these requirements.
CQC has in place the Fundamental Standards which are minimum standards of care for the delivery of services within a regulated activity. These require organisations manage personal information sensitively, confidentially, and appropriately, including respecting the privacy of service users.
CQC requires organisations to have in place policies and procedures for the sharing of information between staff and other agencies (see the ‘Working with Other Care Providers Policy’), managing confidential information, breaches of confidentiality, and the storage and administrative handling of confidential material and records.
Please also see:
1. Data Protection and GDPR Policy
2. Data Quality Policy
3. Data Security Policy
4. Record Keeping Policy
Every person using the service must have their care needs thoroughly assessed before services are provided, with a care plan developed and in place to ensure their needs are identified and met.
Staff who carry out an assessment, or handle assessment/care planning or other material sent to us from other agencies, have access to personal and confidential information about a service user.
It is the duty of such staff to retain, record and share through the care plan and other documents, the information care workers require to meet the service users care and support needs. A similar obligation applies to staff involved in a review or reassessment of care needs or in making any changes in the service provided or escalating concerns to health or social care professionals.
The person using the service has the right to see their records and should be asked to check they agree with everything written in their personal care and support plan before being asked to agree and sign it.
The care workers assisting a service user has access both to the information passed to them when they start to work with that service user and knowledge which accumulates in the course of providing care. They have a duty of confidentiality:
1. To treat all personal information with respect and in the best interests of the service user to whom it relates.
2. To share with their manager, when appropriate, information given to them in confidence if there are concerns or changing needs of the service user.
3. To share pertinent confidential information when required with colleagues with whom they are sharing the task of providing care.
4. To pass and receive confidential information to and from colleagues on occasions when they have to be replaced because of sickness, holidays or other reasons, in a responsible and respectful manner.
5. Only to pass confidential information to other social and healthcare professionals/agencies with the agreement of the service user, with the permission of their manager, or in emergencies when it is clear that it is in the interests of the person using the service or is urgently required for the protection of the person using the service or another person (i.e. compliant with DPA 2018 Code of Practice).
6. To refer to confidential information in training or group supervision sessions with respect and caution and in ways which conceal the identity of the service user to which it relates.
7. Never to gossip about a service user or to pass information to any other individual other than for professional reasons.
8. It is a condition of employment that staff do not disclose confidential information to an unauthorised person. Depending on the breach this could be classed as gross misconduct and lead to a disciplinary matter, and even dismissal (see the ‘Disciplinary Policy’).
Confidential information must occasionally be seen by staff other than the care workers providing direct care. It is therefore the responsibility of managers to ensure that information is stored and handled in ways that limit access to those who have a need to know, and to provide the following arrangements in particular:
1. To provide lockable filing cabinets to hold service users’ records and ensure that records are kept secure at all times.
2. To arrange for information held on computers to be accessed only by appropriate personnel, e.g. through the use of password protection which allows only access to pertinent files relevant to the individual’s role.
3. To locate office machinery and provide appropriate monitor shielding so that screens displaying personal data are hidden from general view.
4. To ensure paperwork is not left lying where anyone can read it.
5. To ensure paperwork is not taken from the office unless absolutely necessary.
There are rare occasions on which it is necessary for a staff member, acting in good faith to breach confidentiality in an emergency situation, for example to protect the service user or another person from grave danger without obtaining the permission of the person to whom it applies.
In such a situation, the staff member should use their best judgment, should consult the service user’s representative, a manager or a colleague if possible, and should inform their manager of what has happened as soon as possible.
As discussed, the organisation will share information where there is a need to protect, safeguard, and support the health and well-being of the service user or carer, and where it would be more harmful not to share information. Staff and the organisation will work in the best interests of the service user and will share information in line with the DPA 2018 Code of Practice.
All people have a right to ask an organisation what information that organisation holds on them, and this is called a Subject Access Request (SAR).
The organisation must comply with a SAR without delay and at the latest within one month of receipt of the request or within one month of the receipt of any information requested to confirm the requester’s identity.
All staff should be aware of the following with regards to requests for information from third parties:
1. Never give out information about service users or team members to others, but pass the SAR request to the Registered Manager.
2. All requests for person identifiable data other than from those engaged in the care of the individual are classed as Subject Access Requests. As a result, the Registered Manager or other appropriate data controller should be notified as soon as possible, as such requests must be complied with within strict statutory timescales.
If a request for information is made by telephone, all team members should:
1. Always try to check the identity of the caller.
2. Check whether they are entitled to the information they request.
3. Take a number, verify it independently and call back if necessary.
4. This includes requests by people claiming to be officials, e.g. Police or CQC inspectors.
Requests for information from the Police or media should always be referred to the Manager in the first instance, and Caldicott Guardian, senior manager or director where appropriate.
If the Crime and Disorder Act 1998 is being implemented the full contact details of the police officer in charge of the case should be obtained and the request be passed to the Registered Manager who will escalate to appropriate members of the senior management team.
In order to comply with the Data Protection Act, a clear desk policy must be enforced. A clear desk policy is keeping personal information secure and restricted to the minimum number of viewers possible. When you leave your desk, you should ensure that any personal or confidential information is not left lying around for others to see. Lock it away in a cupboard or drawer if leaving your desk. Computers should be switched to screen lock as a minimum.
Confidential information must never be sent via external email, either as part of the message or attached as a Word, Excel or other document, which contains personal information about service users or staff, unless the email is encrypted at both ends of the communication or is password protected using an agreed standard. Emails sent to and from health and social care organisations must meet the secure email standard (DCB1596) so that everyone can be sure that sensitive and confidential information is kept secure. You can find out more about the standard, and the action you must take at ‘The secure email standard (https://digital.nhs.uk/services/nhsmail/the-secure-email-standard#top),’ NHS Digital.
One of the largest risks with email is misdirection as a result of human error. Where possible, copy and paste the email address from a recorded source to avoid mis-typing the email address. When communicating sensitive information, a test email should always be sent first, with the information only provided once the recipient has confirmed receipt of the test email. Take your time when emailing personal information, pause and check the email address, email trail and any attachments, and ensure no one other than the recipient has accidentally been included in the ‘to’ or ‘cc’ fields. If you are unsure you should check if the recipient’s email address is secure and that they know the nature of the information being transmitted.
The Data Security and Protection Toolkit is an online self-assessment tool that allows organisations to measure their performance against the National Data Guardian’s 10 data security standards.
All organisations that have access to NHS patient data and systems must use this toolkit to provide assurance that they are practising good data security and that personal information is handled correctly. You can find out more about the toolkit at ‘Data Security and Protection Toolkit (https://beta.digitisingsocialcare.co.uk/data-security-and-protection-toolkit)’, NHS Digital.
Care should be taken to practice good data security when transmitting personal, sensitive or confidential information.
Digital Social Care work in partnership with NHS Digital to support adult social care providers to support their digital transformation. They have a range of free supported resources and guidance which can be accessed at ‘Digitising Social Care (https://beta.digitisingsocialcare.co.uk/).’
You can also find useful information and resources at the ‘Digital Care Hub (https://www.digitalcarehub.co.uk/)’ (the new name for Digital Social Care).
The company’s standard disclaimer should always be in evidence on emails sent by you.
You should not breach any copyright or intellectual information when transmitting information.
You should not send any inappropriate material to any party which could be deemed to be offensive, abusive, obscene, discriminatory, harassing, defamatory or derogatory, whether or not the recipient indicates they would not object. If you receive any transmission which you deem to be offensive or upsetting, you should immediately notify your Line Manager.
Additionally, you should not:
1. Use the system for personal use
2. Send or forward chain mail, junk mail, jokes, gossip etc.
3. Use the system for trivial and unnecessary messages
You must not visit any site or download any information which is illegal, immoral, offensive, abusive, obscene, discriminatory, harassing, defamatory or derogatory. If you have reason to believe a member of staff of doing so, you should report your concerns to your Line Manager as soon as possible.
You should not attempt to access any information which you know is restricted and you are not authorised to view.
Personal use of our internet system is forbidden.
We reserve the right to intercept and read all emails and attachments sent via the company email and internet system and/or using a company email address provided to a staff member.
The organisation will monitor the use of our email and internet system, including where appropriate opening and reading emails (in line with Data Protection legislation). It is therefore important that you do not send any personal emails, particularly of a sensitive or embarrassing nature.
We will monitor usage to ensure:
1. Company policies, standards and guidelines are being followed
2. To provide evidence of transmissions and communication
3. To ensure there is no unauthorised usage
Inappropriate use of the company email and internet system, e.g. sending pornography or other offensive material, will lead to disciplinary action in line with our ‘Disciplinary Policy.’ Depending on the severity of the circumstances, it could lead to your summary dismissal.
Managers and staff are required to follow the appropriate codes of conduct at all times relevant to their professional and work groups, which for this organisation includes:
Skills for Care: Code of Conduct for Healthcare Support Workers and Adult Social Care Workers in England (https://www.skillsforcare.org.uk/Support-for-leaders-and-managers/Managing-people/Code-of-Conduct.aspx)
The Code of Conduct sets out the required behaviour and professional boundaries expected of staff when working for the organisation and delivering services to adults at risk within the community.
Section 5 of the code provides guidance for staff on ‘Respecting People’s Right to confidentiality’ and states:
1.Treat all information about people who use health and care services and their carers as confidential.
2. Only discuss or disclose information about people who use health and care services and their carers in accordance with legislation and agreed ways of working.
3. Always seek guidance from a senior member of staff regarding any information or issues that you are concerned about.
4. Always discuss issues of disclosure with a senior member of staff.
Breaching professional boundaries and/or this policy could have consequences from a safeguarding perspective, could lead to allegations of abuse and could lead to staff being disciplined through our ‘Disciplinary Policy.’
In addition, staff must not share personal information about other staff or confidential information about the company on any social media platform or other communication service that could bring them, their colleagues or the organisation into disrepute, or which is personal information and/or breaches the Data Protection Act 2018 (See also our ‘Social Media Policy’).
Respect people’s right to privacy and confidentiality as in the Nursing and Midwifery Code of Professional Conduct.
As a nurse, midwife or nursing associate, you owe a duty of confidentiality to all those who are receiving care. This includes making sure that they are informed about their care and that information about them is shared appropriately.
To achieve this, you must:
1. Respect a person’s right to privacy in all aspects of their care.
2. Make sure that service users are informed about how and why information is used and shared by those who will be providing care.
3. Respect that a person’s right to privacy and confidentiality continues after they have died – see the ‘End of Life Policy.’
4. Share necessary information with other health and care professionals and agencies only when the interests of patient safety and public protection override the need for confidentiality.
5. Share with service users, their families and their carers, as far as the law allows, the information they want or need to know about their health, care and ongoing treatment sensitively and in a way they can understand.
Breaches of the confidentiality policy could lead to disciplinary action in line with our ‘Disciplinary Policy.’ Depending on the severity of the circumstances, it could lead to your summary dismissal.
Professional standards of practice and behaviour for nurses, midwives and nursing associates, NMC (https://www.nmc.org.uk/standards/code/)
Code of Conduct for Healthcare Support Workers and Adult Social Care Workers in England, Skills for Care
(https://www.skillsforcare.org.uk/Support-for-leaders-and-managers/Managing-people/Code-of-Conduct.aspx)
Data Protection (https://www.gov.uk/data-protection)
Subject Access Request, ICO (https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/right-of-access/what-should-we-consider-when-responding-to-a-request/)
Data Sharing Code of Practice, ICO (https://ico.org.uk/for-organisations/guide-to-data-protection/ico-codes-of-practice/data-sharing-a-code-of-practice/)
Information Sharing Policy, NHS (https://www.england.nhs.uk/wp-content/uploads/2019/10/information-sharing-policy-v4.1.pdf)
Special Category Data, ICO (https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/lawful-basis-for-processing/special-category-data/)
Confidentiality Policy 2019, NHS (https://www.england.nhs.uk/wp-content/uploads/2019/10/confidentiality-policy-v5.1.pdf)
The secure email standard, NHS Digital (https://digital.nhs.uk/services/nhsmail/the-secure-email-standard#top)
Data Security and Protection Toolkit (https://beta.digitisingsocialcare.co.uk/data-security-and-protection-toolkit)
Digital Care Hub (https://www.digitalcarehub.co.uk/)
Digital Care Hub Resources (https://www.digitalcarehub.co.uk/resources/)
Data Security and Protection Toolkit, NHS (https://www.dsptoolkit.nhs.uk/)
Digitising Social Care (https://beta.digitisingsocialcare.co.uk/)
Information sharing in social care, NHS Transformation Directorate (https://transform.england.nhs.uk/information-governance/guidance/information-sharing-in-social-care/)
Key principles of confidentiality, HCPC (https://www.hcpc-uk.org/standards/meeting-our-standards/confidentiality/guidance-on-confidentiality/key-principles-of-confidentiality/)
Safeguarding adults: sharing information, SCIE (https://www.scie.org.uk/safeguarding/adults/practice/sharing-information/)
A Guide to Confidentiality in Health and Social Care, NHS Digital (https://digital.nhs.uk/data-and-information/looking-after-information/data-security-and-information-governance/codes-of-practice-for-handling-information-in-health-and-care/a-guide-to-confidentiality-in-health-and-social-care)
Privacy and dignity in care, SCIE (https://www.scie.org.uk/providing-care/dignity-in-care/privacy/)
We work with people to understand what being safe means to them as well as with our partners on the best way to achieve this. We concentrate on improving people’s lives while protecting their right to live in safety, free from bullying, harassment, abuse, discrimination, avoidable harm and neglect. We make sure we share concerns quickly and appropriately.
We always treat people with kindness, empathy and compassion and we respect their privacy and dignity. We treat colleagues from other organisations with kindness and respect.
We provide appropriate, accurate and up-to-date information in formats that we tailor to individual needs.
We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.
Key questions and quality statements – Care Quality Commission
(https://www.cqc.org.uk/assessment/quality-statements)
Confidentiality Do’s and Don’ts (Cited from the ‘NHS England and NHS Improvement Confidentiality Policy’)
Do’s
1. Do safeguard the confidentiality of all person-identifiable or confidential information that you come into contact with. This is a statutory obligation on everyone working on or behalf of NHS England or NHS Improvement.
2. Do clear your desk at the end of each day, keeping all non-digital records containing person-identifiable or confidential information in recognised filing and storage places that are locked at times when access is not directly controlled or supervised.
3. Do switch off computers with access to person-identifiable or business confidential information, or put them into a password protected mode, if you leave your desk for any length of time.
4. Do ensure that you cannot be overheard when discussing confidential matters.
5. Do challenge and verify where necessary the identity of any person who is making a request for person-identifiable or confidential information and ensure they have a need to know.
6.Do share only the minimum information necessary.
7. Do transfer person-identifiable or confidential information securely when necessary, i.e. use an nhs.net email account to send confidential information to another nhs.net email account or to a secure government domain, e.g. gov.uk.
8. Do seek advice if you need to share patient/person-identifiable information without the consent of the patient/identifiable person’s consent and record the decision and any action taken.
9. Do report any actual or suspected breaches of confidentiality.
10. Do participate in induction, training and awareness raising sessions on confidentiality issues.
Don’ts
1. Don’t share passwords or leave them lying around for others to see.
2. Don’t share information without the consent of the person to which the information relates, unless there are statutory grounds to do so.
3. Don’t use person-identifiable information unless absolutely necessary, anonymise the information where possible.
4. Don’t collect, hold or process more information than you need, and do not keep it for longer than necessary.


Saying Yes And Saying No
Giving consent means saying YES or NO to something.
Before anyone helps you with something, they must ask if it is ok.
People who may ask for your consent include:
1. Your carer or support worker
2. A doctor
3. A nurse
4. A social worker

Consent is when you say YES when you are asked to make a decision.
Saying NO means you do not give consent.

You have the right to make your own decisions
A decision is when you are asked to decide YES or NO about a question or when choosing something.
There are lots of things you can say Yes or No to like:

1. Where you live
2. Who supports you
3. Your care plan
4. What you do
5. Taking your medicines
6. Staff taking photographs of you
Also, sometimes a doctor or a nurse might need your consent for
medical treatment like:

1. An injection
2. An operation
3. New medicines

If you say YES you are Giving Consent

When you make any decision, you can ask questions to help you understand

You can ask what will happen if you say NO

You can ask what will happen if you say YES

You can ask the person to speak to someone else for you

This person might be someone who can help you understand.

You have the right to say No

Having a right means that the law says you can do this
You can say YES or NO in lots of different ways

You can say YES or NO

You can say Yes or No by nodding and shaking your head or by putting your thumbs up or down.
You can say YES or NO by writing a cross or tick

If you are not able to understand someone else can make the decision for you

This decision MUST be what is best for you and is known as a Best Interests Decision

The Law says that this is the only time someone can say YES or NO for you
Health and Social Care Act 2008 (Regulated Activities) Regulations 2014 [17]
Learning culture
Safeguarding
Safe environments
Safe and effective staffing
Consent to care and treatment
Kindness, compassion and dignity
Providing information
Shared direction and culture
Governance, management and sustainability
Please see the ‘Quality Statements’ section for full guidance
This policy includes in its scope all data which we process either in hardcopy or digital copy, this includes special categories of data.
This policy applies to all staff, including temporary staff and contractors.
The organisation is registered with the Information Commissioner’s Office ZA215225.
Please see ‘ICO – Contact us (https://ico.org.uk/global/privacy-notice/how-you-can-contact-us/).’
This policy and procedure are provided for the regulated activity of personal care.
Our organisation is committed to equal rights and the promotion of choice, person-centred care and independence. This policy demonstrates our commitment to creating a positive culture of respect for all individuals. The intention is, as required by the Equality Act 2010, to identify, remove or minimise discriminatory practice in the nine named protected characteristics of age, disability, sex, gender reassignment, pregnancy and maternity, race, sexual orientation, religion or belief, and marriage and civil partnership. It is also intended to reflect the Human Rights Act 1998 to promote positive practice and value the diversity of all individuals.
1. We have in place robust arrangements for the availability, integrity and confidentiality of data, records and data management systems. Information is used effectively to monitor and improve the quality of care.
2. We recognise data protection as a fundamental right and embrace the principles of data protection by design and by default. This policy includes in its scope all data which we process either in hardcopy or digital copy; this includes special categories of data.
3.We will establish and maintain policies to ensure compliance with the Data Protection Act 2018, Human Rights Act 1998, the common law duty of confidentiality, the UK General Data Protection Regulation and all other relevant legislation.
4. The Caldicott Principles are embedded within the organisation to ensure confidentiality and the sharing of information to promote safe and effective care provision.
5. Caldicott Guardians are senior people within an organisation who protect the confidentiality of people’s information by considering the ethical and legal aspects of data sharing. Previously only NHS and local authority bodies were required to have a Caldicott Guardian. Guidance issued in August 2021 requires adult social care services who provide a publicly funded service to appoint a Caldicott Guardian.
6. All staff are required to read and comply with this policy, and any breach of the policy may be deemed as gross misconduct and be managed under the organisations disciplinary policies.
7. The organisation will use resources including ICO and Digital Care Hub to ensure policies and procedures are updated in line with the latest legislation, regulations, and guidance to ensure service user and staff data is secure and well managed.
8. All CQC-registered care providers should complete the Data Security and Protection Toolkit (DSPT) at least once a year (See references). It is also a requirement to submit the toolkit if you deliver services under a NHS contract, use a shared health and care record, or are applying for NHSMail. The DSPT has an annual deadline for completion every year. Please see ‘Better Security, Better Care, Digital Care Hub (https://www.digitalcarehub.co.uk/data-security-protecting-my-information/better-security-better-care/)’ for further information on the annual completion date requirements and supportive resources.
This policy must be read and implemented by all staff, managers and directors of the organisation.
The organisation has in place robust arrangements for the availability, integrity and confidentiality of data, records and data management systems. Information is used effectively to monitor and improve the quality of care, to keep service users safe, and deliver a caring, responsive, effective and well-led service.
This ‘Data Protection Policy’ is the overarching policy for data security and protection for Aroma Care (hereafter referred to as ‘us,’ we,’ or ‘our’).
1. We are registered with ICO and use its guides to legislation to support the organisation’s practice in data management, security and record keeping.
2. We will be open and transparent with service users and those who lawfully act on their behalf in relation to their care and treatment. We will adhere to our duty of candour responsibilities as outlined in the Health and Social Care Act 2012.
3. We will establish and maintain policies to ensure compliance with the Data Protection Act 2018, Human Rights Act 1998, the common law duty of confidentiality, the UK General Data Protection Regulation and all other relevant legislation.
4. We will establish and maintain policies for the controlled and appropriate sharing of service user and staff information with other agencies, taking account all relevant legislation and citizen consent.
5. Where consent is required for the processing of personal data we will ensure that informed and explicit consent will be obtained and documented in clear, accessible language and in an appropriate format. The individual can withdraw consent at any time through processes which have been explained to them and which are outlined in our ‘Record Keeping Policy: Withdrawal of Consent’ procedures. We ensure that it is as easy to withdraw as to give consent.
6. We will undertake annual audits of our compliance with legal requirements.
We acknowledge our accountability in ensuring that personal data shall be:
1. Processed lawfully, fairly and in a transparent manner
2. Collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes
3. Adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed (‘data minimisation’)
4. Accurate and kept up to date
5. Kept in a form which permits identification of data subjects for no longer than is necessary for the purposes for which the personal data are processed (‘storage limitation’)
6. Processed in a manner that ensures appropriate security of the personal data.
We uphold the personal data rights outlined in the UK GDPR:
1. The right to be informed
2. The right of access
3. The right to rectification
4. The right to erasure
5. The right to restrict processing
6. The right to data portability
7. The right to object
10. Rights in relation to automated decision making and profiling.
Due to our size, we have determined that we are not required to have a Data Protection Officer (DPO), as we do not process special categories of data on a large scale. Nonetheless, to ensure that every individual’s data rights are respected and that there are the highest levels of data security and protection in our organisation, we have appointed a member of staff to the Data Protection Champion role. The Data Protection Champion will report to the highest management level of the organisation. We will support the Data Protection Champion with the necessary resources to carry out their tasks and ensure that they can maintain expertise.
NB: You should make sure that there is somebody who is responsible for data security and protection within your organisation, though you do not have to call them a Data Protection Champion.
This policy is underpinned by the following:
1. Data Quality Policy – outlines procedures to ensure the accuracy of records and the correction of errors.
2. Record Keeping Policy – details transparency procedures, the management of records from creation to disposal (inclusive of retention and disposal procedures), information handling procedures, procedures for subject access requests, right to erasure, right to restrict processing, right to object, and withdrawal of consent to share.
3. Data Security Policy – outlines procedures for the ensuring the security of data including the reporting of any data security breach.
4. Network Security Policy – outlines procedures for securing our network.
5. Business Continuity Plan –outlines the procedures in the event of a security failure or disaster affecting digital systems or mass loss of hardcopy information necessary to the day to day running of our organisation.
6. Staff Data Security Code of Conduct (https://view.officeapps.live.com/op/view.aspx?src=https%3A%2F%2Fwww.digitalcarehub.co.uk%2Fwp-content%2Fuploads%2F2019%2F04%2FStaff-Data-Security-and-Protection-Code-of-Conduct-Template-v3.docx&wdOrigin=BROWSELINK) – provides staff with clear guidance on the disclosure of personal information.
7. Surveillance Equipment & CCTV Policy – sets out the safe procedures and principles for considering and using CCTV and other surveillance equipment.
We shall implement appropriate organisational and technical measures to uphold the principles outlined above. We will integrate necessary safeguards to any data processing to meet regulatory requirements and to protect individual’s data rights. This implementation will consider the nature, scope, purpose and context of any processing and the risks to the rights and freedoms of individuals caused by the processing.
We shall uphold the principles of data protection by design and by default from the beginning of any data processing and during the planning and implementation of any new data process. Prior to starting any new data processing, we will assess whether we should complete a Data Protection Impact Assessment (https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/accountability-and-governance/data-protection-impact-assessments/) (DPIA) using the ICO’s screening checklist:
1. All new systems used for data processing will have data protection built in from the beginning of the system change.
2. All existing data processing has been recorded on our Record of Processing Activities. Each process has been risk assessed and is reviewed annually.
3. We ensure that, by default, personal data is only processed when necessary for specific purposes and that individuals are therefore protected against privacy risks.
4. In all processing of personal data, we use the least amount of identifiable data necessary to complete the work it is required for and we only keep the information for as long as it is required for the purposes of processing or any other legal requirement to retain it.
Where possible, we will use pseudonymised data to protect the privacy and confidentiality of our staff and those we support.
Our designated Data Protection Champion is Alison Bullous. The key responsibilities of the lead are:
1. To ensure the rights of individuals in terms of their personal data are upheld in all instances and that data collection, sharing and storage is in line with the Caldicott Principles.
2. To define our data protection policy and procedures and all related policies, procedures and processes and to ensure that sufficient resources are provided to support the policy requirements.
3. To complete the ‘Data Security & Protection Toolkit (https://www.dsptoolkit.nhs.uk/)‘ (DSPT) annually and to maintain compliance with the DSPT. The deadline for 2021/22 was 30 June 2022.
4. To monitor information handling to ensure compliance with law, guidance and the organisation’s procedures and liaising with senior management and DPO to fulfil this work.
Our designated Data Protection Officer is Alison Bullous, they can be contacted via email: [email protected]; phone: 07940 098709; or at the following address: Aroma Care, Dale House, The Hollow, Lutterworth, Leicestershire LE17 4BL. The key responsibilities of the DPO are: Overseeing changes to systems and processes, Monitoring compliance with the GDPR and the Data Protection Act 2018, Completing DPIA, Reporting on data protection and compliance with legislation to senior management, Liaising, if required, with the Information Commissioner’s Office (ICO).
Surveillance technology includes CCTV, cameras and microphones. It can help keep people safe and monitor their care. If used, it is important it is done in a way that protects people’s privacy and human rights.
Surveillance technology can help:
1. Protect people’s safety, for example from the risk of unsafe care or treatment.
2. Keep premises and property secure.
3. To help people stay safe without restricting their activities.
4. Please see ‘Surveillance Equipment & CCTV Policy.’
The overarching aim of the organisation is to ensure that there is an appropriate balance between the protection of the service user’s information, and the use and sharing of such information to improve care.
All staff will be trained through information governance training on the Caldicott Principles and how these support the Data Protection Act 2018 and UK GDPR.
Staff are required to incorporate the following principles within their practice, and managers will through training, supervision, and appraisal ensure that staff are competent in data protection, UK GDPR and the Caldicott Principles.
Caldicott Guardians are senior people within an organisation who protect the confidentiality of people’s information by considering the ethical and legal aspects of data sharing. Previously only NHS and local authority bodies were required to have a Caldicott Guardian. Guidance issued in August 2021 requires adult social care services who provide a publicly funded service to appoint a Caldicott Guardian. It may not be feasible or proportionate for some organisations to have a Caldicott Guardian. Some organisations may choose to share a Caldicott Guardian. Some organisations may agree with a commissioner that they will access the commissioning organisation Caldicott Guardian for advice whenever necessary. The National Data Guardian (NDG) has provided guidance on the appointment of Caldicott Guardians.
NDG – Guidance about the appointment of Caldicott Guardians (https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/1013756/Caldicott_Guardian_guidance_v1.0_27.08.21.pdf)
All Caldicott Guardians need to be registered on the Caldicott Guardian’s registered which is maintained by NHS digital.
The Eight Caldicott Principles, National Data Guardian (https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/942217/Eight_Caldicott_Principles_08.12.20.pdf)
Every proposed use or transfer of confidential information should be clearly defined, scrutinised and documented, with continuing uses regularly reviewed by an appropriate guardian.
Confidential information should not be included unless it is necessary for the specified purpose(s) for which the information is used or accessed. The need to identify individuals should be considered at each stage of satisfying the purpose(s) and alternatives used where possible.
Where use of confidential information is considered to be necessary, each item of information must be justified so that only the minimum amount of confidential information is included as necessary for a given function.
Only those who need access to confidential information should have access to it, and then only to the items that they need to see. This may mean introducing access controls or splitting information flows where one flow is used for several purposes.
Action should be taken to ensure that all those handling confidential information understand their responsibilities and obligations to respect the confidentiality of patient and service users.
Every use of confidential information must be lawful. All those handling confidential information are responsible for ensuring that their use of and access to that information complies with legal requirements set out in statute and under the common law.
Health and social care professionals should have the confidence to share confidential information in the best interests of patients and service users within the framework set out by these principles. They should be supported by the policies of their employers, regulators and professional bodies.
A range of steps should be taken to ensure no surprises for patients and service users, so they can have clear expectations about how and why their confidential information is used, and what choices they have about this. These steps will vary depending on the use: as a minimum, this should include providing accessible, relevant and appropriate information – in some cases, greater engagement will be required.
Please note: this policy has been adapted from the Digital Care Hub Data Protection policy template (https://www.digitalcarehub.co.uk/resource/data-protection-policy-template/)
The Data Protection Act 2018 (https://www.gov.uk/data-protection)
Data Protection and Security Toolkit, NHS (https://www.dsptoolkit.nhs.uk/)
Handling personal information, CQC (https://www.cqc.org.uk/guidance-providers/all-services/check-way-you-handle-personal-information-meets-right-standards-0)
Information Commissioner’s Office (https://ico.org.uk/)
Digital Social Care (https://www.digitalsocialcare.co.uk/)
Data protection impact assessments, ICO (https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/accountability-and-governance/data-protection-impact-assessments/)
A guide to good practice for digital and data-driven health technologies (http://www.gov.uk/government/publications/code-of-conduct-for-data-driven-health-and-care-technology/initial-code-of-conduct-for-data-driven-health-and-care-technology#principle-1-understand-users-their-needs-and-the-context)
Data Security and Protection Toolkit Key roles and the DPO, NHS (https://www.dsptoolkit.nhs.uk/Help/Attachment/61)
Using surveillance in your care service, CQC (https://www.cqc.org.uk/guidance-providers/all-services/using-surveillance-your-care-service)
The Eight Caldicott Principles, National Data Guardian (https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/942217/Eight_Caldicott_Principles_08.12.20.pdf)
Caldicott-guardians-what-social-care-providers-need-to know, Digitising Social Care (https://beta.digitisingsocialcare.co.uk/news/caldicott-guardians-what-social-care-providers-need-know-about-need-know)
Better Security, Better Care, Digital Care Hub (https://www.digitalcarehub.co.uk/data-security-protecting-my-information/better-security-better-care/)
We have a proactive and positive culture of safety based on openness and honesty, in which concerns about safety are listened to, safety events are investigated and reported thoroughly, and lessons are learned to continually identify and embed good practices.
We work with people to understand what being safe means to them as well as with our partners on the best way to achieve this. We concentrate on improving people’s lives while protecting their right to live in safety, free from bullying, harassment, abuse, discrimination, avoidable harm and neglect. We make sure we share concerns quickly and appropriately.
We detect and control potential risks in the care environment. We make sure that the equipment, facilities and technology support the delivery of safe care.
We make sure there are enough qualified, skilled and experienced people, who receive effective support, supervision and development. They work together effectively to provide safe care that meets people’s individual needs.
We tell people about their rights around consent and respect these when we deliver person-centred care and treatment.
We always treat people with kindness, empathy and compassion and we respect their privacy and dignity. We treat colleagues from other organisations with kindness and respect.
We provide appropriate, accurate and up-to-date information in formats that we tailor to individual needs.
We have a shared vision, strategy and culture. This is based on transparency, equity, equality and human rights, diversity and inclusion, engagement, and understanding challenges and the needs of people and our communities in order to meet these.
We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.
Key questions and quality statements – Care Quality Commission (https://www.cqc.org.uk/assessment/quality-statements)
Health and Social Care Act 2008 (Regulated Activities) Regulations 2014 [17,18,19]
Learning culture
Safeguarding
Safe environments
Safe and effective staffing
Consent to care and treatment
Kindness, compassion and dignity
Providing information
Shared direction and culture
Governance, management and sustainability
Please see the ‘Quality Statements’ section for full guidance
This policy includes in its scope all data which the organisation processes, either in hardcopy or digital copy, and includes emails, text and relevant social media formats, e.g. WhatsApp messages and special categories of data. This policy applies to all staff, including temporary staff and contractors.
This policy and procedure are provided for the regulated activity of personal care.
Our organisation is committed to equal rights and the promotion of choice, person-centred care and independence. This policy demonstrates our commitment to creating a positive culture of respect for all individuals. The intention is, as required by the Equality Act 2010, to identify, remove or minimise discriminatory practice in the nine named protected characteristics of age, disability, sex, gender reassignment, pregnancy and maternity, race, sexual orientation, religion or belief, and marriage and civil partnership. It is also intended to reflect the Human Rights Act 1998 to promote positive practice and value the diversity of all individuals.
1. We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.
2. We will ‘maintain securely an accurate, complete and contemporaneous record in respect of each service user, including a record of the care and treatment provided to the service user and of decisions taken in relation to the care and treatment provided.’
3. The principal purpose of service user records is to record and communicate information about the individual and their care.
4. In line with national legislation, individuals have the right to have access to their personal data which we process and store. Service users have the right to the rectification of said records in the instance that their records are inaccurate or incomplete.
5. A record of all rectification requests and outcomes will be kept by the Data Security and Protection Lead and/or Registered Manager in line with timeframes outlined in the ‘Records management: code of practice for health and social care (https://www.gov.uk/government/publications/records-management-code-of-practice-for-health-and-social-care).’
The availability of high quality, accurate and timely data is vital for the safety of the people we care for and the safe and responsible running of our organisation. This policy outlines the following procedures:
1. Procedures for ensuring data accuracy
2. Procedures for correcting errors
This organisation commits to ensuring it will comply with the Health and Social Care Act 2008 (Regulated Activities) Regulations 2014: Regulation 17 that it will ‘maintain securely an accurate, complete and contemporaneous record in respect of each service user, including a record of the care and treatment provided to the service user and of decisions taken in relation to the care and treatment provided.’
We ensure accuracy in our data in both hardcopy and digital records by making sure all data has the
following characteristics:
Authentic – the data is what it claims to be, has been created or sent by the person who said that they created or sent it, and that this was done at the time claimed.
Reliable – the data is complete, accurate, has been created close to the time of the activity it records, and has been created by individuals with direct knowledge of the event it records.
Integrity – the data is complete and unaltered; it is also protected from being changed or altered by unauthorised persons; any alterations are clearly marked and the person who made them can be identified.
Useable – the data can be located when it is required for use and its context is clear in a contemporaneous record.
The principal purpose of service user records is to record and communicate information about the individual and their care to ensure that the delivery of the service is safe, meets their needs, takes into account relevant risks and mitigation, identifies their choices and preferences, and provides dignity and respect.
The principal purpose of staff records is to record employment details for payroll and business planning purposes, ensure staff meet the rigorous standards for fit and proper persons (Regulation 19), e.g. enhanced DBS, record relevant qualifications, skills and experience (Regulation 18), as well as supervision and performance management to identify and maintain competence to practice.
To fulfil these purposes, we:
1. Use standardised structures and layouts for the contents of records.
2. Ensure documentation reflects the continuum of care, that all care is person-centred and that care records are viewable in chronological order.
3. Provide a clearly written care plan when care is being delivered by several members of the team, and we ensure that records are maintained and updated and shared with everyone involved.
4. Train staff on the creation and use of records and provide annual training on Information Governance which includes good record keeping.
5. Have implemented a procedure that enables service users and staff to have easy access to their records where appropriate. This is outlined in the ‘Record Keeping Policy’ and our Privacy Notice.
6. Ensure that all staff who record information, whether hardcopy or electronic, know that they have a contractual responsibility to ensure that the data is accurate and as complete as possible. This responsibility extends to any system the staff member has access to.
In line with national legislation, individuals have the right to have access to their personal data which we process and store. Service users have the right to the rectification of said records in the instance that their records are inaccurate or incomplete.
Where at all possible, in the instance that we have appropriately shared that individual’s records with any third-party, we will inform this third-party of the rectification if appropriate.
In all cases, we will respond to a request for rectification within one month. Should the request be complex this may be extended to two months. However, we will inform the individual within one month in writing of the extension and the reasons why it is required.
To request for their records to be rectified, service users or staff should contact us with the request for rectification either verbally or in writing. Individuals can ask anyone in your organisation to request this, so staff should know their responsibilities to pass on requests to the Data Security and Protection Lead and/or Registered Manager in a timely manner. If the rectification is due to the record being incomplete, then the individual should provide the supplementary information to update the record.
While we are assessing the request to rectify records, we will restrict processing of the data in question. This will be done in line with our Right to Restrict Processing Procedure as outlined in our ‘Record Keeping Policy.’
A record of all rectification requests and outcomes will be kept by the Data Security and Protection Lead and/or Registered Manager in line with timeframes outlined in the‘ Records Management Code of Practice (https://transform.england.nhs.uk/information-governance/guidance/records-management-code/records-management-code-of-practice/)’ which provides guidance on how to keep records, including how long to keep different types of records. Note: if the organisation has its own retention schedule which no longer conforms to legislation and recommended practice this is acceptable. However, you must include where the organisation stores the retention schedule.
See,the Data Quality Template v6, Digital Care Hub (https://www.digitalcarehub.co.uk/resource/data-quality-policy-template/).’
1. All individuals who have their rectification request refused will be informed of their legal rights to complain to the ICO and to seek a judicial remedy.
2. All staff will be informed of this policy.
3. All service users, or their legal representative, will be informed of this policy, as well as their other rights as regards their personal data, when they sign initial contracts with us.
4. In order to process your request for rectification, you might be asked to provide identifying documents so that we can authenticate that it is appropriate for you to update your data.
The Data Security and Protection Lead, or equivalent job role, has overall responsibility for data quality policies and procedures being reviewed annually and for staff training in data quality and for monitoring data quality throughout the organisation. They also are responsible for responding to rectification requests and recording the outcome of any request.
The Registered Manager is responsible for the quality of all records and making sure that staff understand their commitments in ensuring data quality.
Every member of staff is individually responsible for the quality of data they personally record, whether on paper or electronically. Additionally, they are responsible for reporting any mistakes they do notice to the Data Security and Protection Lead or Registered Manager.
Staff are aware that data accuracy and security is a contractual and legislative requirement, and that breach of this policy might result in disciplinary action.
Please note this policy has been updated from the ‘Data Quality Template v6, Digital Care Hub (https://www.digitalcarehub.co.uk/resource/data-quality-policy-template/).’
A guide to good practice for digital and data-driven health technologies (https://www.gov.uk/government/publications/code-of-conduct-for-data-driven-health-and-care-technology/initial-code-of-conduct-for-data-driven-health-and-care-technology#principle-1-understand-users-their-needs-and-the-context)
Records Management Code of Practice, NHS England (https://www.nhsx.nhs.uk/information-governance/guidance/records-management-code/)
Data Security and Protection Toolkit (https://www.dsptoolkit.nhs.uk/)
Data security: local support, national webinar and film series, Digital Care Hub
(https://www.digitalcarehub.co.uk/data-security-local-support-national-webinar-and-film-series/)
The Caldicott Principles (https://www.gov.uk/government/publications/the-caldicott-principles)
Safe Data, Safe Care, CQC (https://www.cqc.org.uk/publications/themed-work/safe-data-safe-care)
Codes of practice for handling information in health and care, NHS England
(https://digital.nhs.uk/data-and-information/looking-after-information/data-security-and-information-governance/codes-of-practice-for-handling-information-in-health-and-care)
We have a proactive and positive culture of safety based on openness and honesty, in which concerns about safety are listened to, safety events are investigated and reported thoroughly, and lessons are learned to continually identify and embed good practices.
We work with people to understand what being safe means to them as well as with our partners on the best way to achieve this. We concentrate on improving people’s lives while protecting their right to live in safety, free from bullying, harassment, abuse, discrimination, avoidable harm and neglect. We make sure we share concerns quickly and appropriately.
We detect and control potential risks in the care environment. We make sure that the equipment, facilities and technology support the delivery of safe care.
We make sure there are enough qualified, skilled and experienced people, who receive effective support, supervision and development. They work together effectively to provide safe care that meets people’s individual needs.
We tell people about their rights around consent and respect these when we deliver person-centred care and treatment.
We always treat people with kindness, empathy and compassion and we respect their privacy and dignity. We treat colleagues from other organisations with kindness and respect.
We provide appropriate, accurate and up-to-date information in formats that we tailor to individual needs.
We have a shared vision, strategy and culture. This is based on transparency, equity, equality and human rights, diversity and inclusion, engagement, and understanding challenges and the needs of people and our communities in order to meet these.
We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.
Key questions and quality statements – Care Quality Commission (https://www.cqc.org.uk/assessment/quality-statements)
Health and Social Care Act 2008 (Regulated Activities) Regulations 2014 [17,19]
Learning culture
Safeguarding
Safe environments
Safe and effective staffing
Consent to care and treatment
Kindness, compassion and dignity
Providing information
Shared direction and culture
Governance, management and sustainability
Please see the ‘Quality Statements’ section for full guidance
This ‘Data Security Policy’ regards the safeguarding and protection of sensitive personal information and confidential information as is required by law (including, but not limited to, the Data Protection Act 2018, Health & Social Care Act 2012 and 2015, and the Common Law duty of confidentiality).
This policy includes in its scope all data which we process, either in hardcopy or digital copy; this includes special categories of data. This policy applies to all staff, including temporary staff and contractors.
This policy and procedure are provided for the regulated activity of personal care.
Our organisation is committed to equal rights and the promotion of choice, person-centred care and independence. This policy demonstrates our commitment to creating a positive culture of respect for all individuals. The intention is, as required by the Equality Act 2010, to identify, remove or minimise discriminatory practice in the nine named protected characteristics of age, disability, sex, gender reassignment, pregnancy and maternity, race, sexual orientation, religion or belief, and marriage and civil partnership. It is also intended to reflect the Human Rights Act 1998 to promote positive practice and value the diversity of all individuals.
1. We have in place robust arrangements for the availability, integrity and confidentiality of data, records and data management systems. Information is used effectively to monitor and improve the quality of care.
2. This policy includes in its scope all data which we process either in hardcopy or digital copy; this includes special categories of data.
3. Physical access to records shall only be granted on a strict ‘Need to Know’ basis.
4. Our staff must keep personal and confidential data securely in locked storage when not in use and keys should not be left in the barrels of filing cabinets and doors.
5. All offices, when left unoccupied, must be locked unless all personal and confidential information has first been cleared from workstations/desks and secured in locked storage.
6. Confidentiality audits will focus on controls within electronic records management systems and paper record systems, the purpose being to discover whether confidentiality has been breached or put at risk.
In order to mitigate the risks of a security breach we will:
a. Follow the Physical Access, Digital Access, Access Monitoring and Data Security procedures.
b. Ensure our staff are trained to recognise a potential data breach whether it is a confidentiality, integrity or availability breach.
c. The Data Security and Protection Lead and/or Registered Manager will inform any individual that their personal data has been breached if it is likely that there is a substantial risk to their rights and freedoms.
The purpose of this document is to outline how we prevent data security breaches and how we react to them when prevention is not possible. By data breach we mean a security incident in which the confidentiality, integrity or availability of data is compromised. A breach can either be purposeful or accidental. This ‘Data Security Policy’ covers:
1. Physical Access procedures
2. Digital Access procedures
3. Access Monitoring procedures
4. Data Security Audit procedures
5. Data Security Breach procedures
The organisation is committed to the secure and safe management of all Personal Data and Sensitive Personal Data it holds about service users, family members and staff in its lawful pursuit of its business and the delivery of the regulated activity.
Physical access to records shall only be granted on a strict ‘Need to Know’ basis. During their induction each staff member who requires access to confidential information for their job role will be trained on the safe handling of all information and will be taught the procedures which govern how data is used, stored, shared and organised in our organisation. Growing and developing confident and skilled digital leaders will ensure the digital development of those they manage. Staff will be provided with annual update training on Information Governance, including data security.
Staff must retain personal and confidential data securely in locked storage when not in use and keys should not be left in the barrels of filing cabinets and doors.
All offices, when left unoccupied, are locked unless all personal and confidential information has first been cleared from workstations/desks and secured in locked storage.
The Information Asset Register (IAR) contains the location of all confidential and sensitive personal information. Each storage location is risk assessed to ensure that the data is properly secured. This risk assessment forms part of the IAR.
A record is be kept of who has access to each storage location. This record can be found within the IAR.
An audit is completed at least annually by the Registered Manager, or delegated manager, to ensure that information is secured properly, and that access is restricted to those who have a legal requirement to use the information. The details of this audit are outlined in the Data Security Audit Procedures below.
Access shall be granted using the principle of ‘Least Privilege’. This means that every programme and every user of the system should operate using the least set of privileges necessary to complete their job. We will ensure that each user is identified by a unique user ID so that users can be linked to, and made responsible for, their actions.
The use of group IDs is only permitted where they are suitable for the work carried out.
During their induction each staff member who requires access to digital systems for their job role will be trained on the use of the system, given their user login details, and they will be required to sign to indicate that they understand the conditions of access. As discussed, Information Governance training updates will be provided annually.
A record is kept of all users given access to the system. This record can be found in the IAR in the Registered Manager’s Office.
In the instance that there are changes to user access requirements, these can only be authorised by the Data Security and Protection Lead or Registered Manager.
The IAR will contain the location of all confidential and sensitive personal information which is digitally stored.
We will follow robust password management procedures and ensure that all staff are trained in password management. Information Governance training updates will be provided annually.
As soon as an employee leaves, all their system logons are revoked. As part of the employee termination process, the Data Security and Protection Lead and/or Registered Manager is responsible for the removal of access rights from the computer system.
The Data Security and Protection Lead or Registered Manager will review all access rights on a regular basis, but in any event at least once a year. The review is designed to positively confirm all system users. Any lapsed or unwanted user accounts which are identified are disabled immediately and deleted unless positively reconfirmed.
When not in use all screens will be locked, and a clear screen policy will be followed.
The management of digital access rights is subject to regular compliance checks to ensure that these procedures are being followed and that staff are complying with their duty to use their access rights in an appropriate manner. Quarterly supervisions and spot checks will be used to assess compliance.
Areas considered in the compliance check include whether:
1. Allocation of administrator rights is restricted
2. Access rights are regularly reviewed
3. There is any evidence of staff sharing their access rights; staff should know that this can result in disciplinary procedures
4.Staff are appropriately logging out of the system
5. Our password policy is being followed
6. Staff understand how to report any security breaches
Confidentiality audits will focus on controls within electronic records management systems and paper record systems. The purpose of these audits is to discover whether confidentiality has been breached, or put at risk, through deliberate misuse of systems, or as a result of insufficient controls.
Audits of security and access arrangements within each area are to be conducted on a six-monthly rolling programme. How frequently you audit information can vary, but as a minimum there should be a full annual audit.
Audits will be carried out as required by some or all of these methods:
1. Unannounced spot checks to random work areas.
2. A series of interviews with management and staff where a department or area of the organisation have been identified for a confidentiality audit.
3. These audits will be carried out by the Data Security and Protection Lead or Registered Manager.
Information will usually be based on electronic reports from the care planning software, auditing of care plans and other relevant documentation, e.g. MAR records, either from our ICT contractor or from internal monitoring.
Some or all of the following checks will be made during data security audits:
1. The Information Asset Register has been reviewed, updated and signed off.
2. The Record of Processing Activities has been reviewed, updated and signed off.
3. Failed attempts to access confidential information.
4. Repeated attempts to access confidential information.
5. Access of confidential information by unauthorised persons.
6. Previous confidentiality incidents and actions, including any disciplinary action taken.
7.Staff awareness of policies and guidelines concerning confidentiality and understanding of their responsibilities regarding confidentiality.
8. Appropriate communications with service users.
9. Appropriate recording and/or use of consent forms.
10. Appropriate allocation of access rights to confidential information, both hardcopy and digital.
11. Appropriate staff access to physical areas.
12. Storage of, and access to, filed hardcopy service user notes and information.
13. Correct process used to securely transfer personal information by post, fax or email.
14. Appropriate use and security of desk and mobile devices in open areas.
15. Security applied to PCs, laptops and mobile electronic devices.
16. Evidence of secure waste disposal.
17. Appropriate transfer and sharing arrangements are in place.
18. Security and arrangements for recording access applied to manual files both live and archive, e.g. storage in locked cabinets/locked rooms.
19. Appropriate staff use of computer systems, e.g. no excessive personal use, no attempting to download software without authorisation, use of social media, attempted connection of unauthorised devices etc.
Each audit will include a list of the activities undertaken, and action plans will be developed from the results to develop and improve data security and management.
In order to mitigate the risks of a security breach the organisation will:
1. Follow the Physical Access, Digital Access, Access Monitoring and Data Security procedures.
2. Ensure our staff are trained to recognise a potential data breach whether it is a confidentiality, integrity, or availability breach.
3. Ensure our staff understand the procedures to follow and how to escalate a security incident to the correct person in order to determine if a breach has taken place.
4. In the instance that it appears that a data security breach has taken place, the staff member who notices the breach, or potential breach, will complete a Data Security Incident Form without delay.
5. This form will be completed and handed to the Data Security and Protection Lead or Registered Manager or, if they are not available, to a member of senior management.
6. The Data Security and Protection Lead and/or Registered Manager will complete the rest of the Data Security Incident Form and conduct a thorough investigation into the breach.
In the instance that the breach is a personal data breach and it is likely that there will be a risk to the rights and freedoms of an individual then the Information Commissioner’s Office (ICO) will be informed as soon as possible, but at least within 72 hours of our discovery of the breach, via the ‘DSPT Incident Reporting Tool (https://www.dsptoolkit.nhs.uk/Help/29).’
Also see ‘NHS – Data Security and Protection Toolkit (https://www.dsptoolkit.nhs.uk/).’
As part of our report, we will provide the ICO with the following details:
1. The nature of the personal data breach (i.e. confidentiality, integrity, availability).
2. The approximate number of individuals concerned and the category of individual (e.g. employees, mailing lists, service users).
3. The categories and approximate number of personal data records concerned.
4. The name and details of our Data Security and Protection Lead or Registered Manager.
5. The likely consequences of the breach.
6. A description of the measures taken, or which we will take, to mitigate any possible adverse effects.
The Data Security and Protection Lead and/or Registered Manager will inform any individual that their personal data has been breached if it is likely that there is a high risk to their rights and freedoms. We will inform them directly and without any undue delay.
A data security breach must be marked on the IAR and will prompt an audit of all processes in order to correct any procedure which led to the breach.
A record of all personal data breaches will be kept including those breaches which the ICO were not required to be notified about.
The Data Security and Protection Lead or the Registered Manager is responsible for physical security, updating and auditing the IAR and Records of Processing Activities (ROPA), digital access, managing breaches and data security audits.
Please note this policy has been updated from the ‘Digital Care Hub Data Security template (https://www.digitalcarehub.co.uk/resource/data-security-policy-template/).’
If the organisation is bidding for public sector contracts which involve handling sensitive and personal information or the provision of certain technical products and services, they will require Cyber Essentials Certification.
The following link sets out guidance from the National Cyber Security Centre on IT infrastructure, ‘Cyber Essentials: Requirements for IT infrastructure v3.1 (https://www.ncsc.gov.uk/files/Cyber-Essentials-Requirements-for-Infrastructure-v3-1-January-2023.pdf).’
The Data Security and Protection Lead or the Registered Manager will ensure that the following technical controls are in place in compliance with the Cyber Essentials requirements. This is particularly important where Cyber Essentials is a requirement of a publicly awarded contract from local government or NHS.
Please see ‘Updates to the Cyber Essentials Scheme (https://www.gov.uk/government/publications/ppn-0923-updates-to-the-cyber-essentials-scheme).’
Firewalls
Firewalls will be in place within the organisation to protect from unwanted access to the company’s IT systems and networks. The firewalls will monitor all network traffic to identify and block unwanted traffic that could be harmful to the IT systems and networks. The security provided by the firewall will be adjusted to protect boundary firewalls, desktop computers, laptops, routers, servers, and cloud services such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS).
The aim is to make sure that only secure and necessary network services can be accessed from the internet.
As all devices run network services to allow them to communicate with other devices and services, we aim to restrict access to these services, to reduce exposure to attacks from external software and hackers.
This is done by using firewalls or network devices with firewall functionality. For cloud services employed by the organisation we will consider/implement data flow policies to restrict access.
A boundary firewall is a network device which restricts the inbound and outbound network traffic to services on its network of computers and mobile devices. These will be used to protect against cyber attacks by implementing restrictions i.e. ‘firewall rules,’ which will allow or block traffic depending on its source, destination and type of communication protocol.
Where the organisation does not control the network to which a device connects, we will deploy and configure a software firewall to protect the device.
The organisation will:
1. Protect every appropriate device with a correctly configured firewall (or network device with firewall functionality).
2. Where installed, we will deploy the desktop or laptop operating system’s software firewall in preference to a third-party firewall application.
For all firewalls (or network devices with firewall functionality), we will:
1. Change default administrative passwords to a strong and unique password (see ‘Password- based Authentication’) – or disable remote administrative access entirely.
2. Prevent access to the administrative interface (used to manage firewall configuration) from the internet, unless there is a clear and documented business need, and the interface is protected by one of the following controls:
a. Multi-factor authentication (see MFA details below).
b. An IP allow list that limits access to a small range of trusted addresses combined with a properly managed password authentication system.
c. Block unauthenticated inbound connections by default.
d. Ensure inbound firewall rules are approved and documented by an authorised person and include the business need in the documentation.
e. Remove or disable unnecessary firewall rules quickly, when they are no longer needed.
f. Make sure we use a software firewall on devices which are used on untrusted networks, such as public wifi hotspots.
Secure configuration will be applied to servers, desktop computers, laptops, tablets, mobile phones, thin clients, IaaS, PaaS and SaaS.
This will be done to ensure that computers and network devices are properly configured to:
1. Reduce vulnerabilities
2. Provide only the services required to fulfil their role
The default configurations of computers and network devices are not always secure because out- of-the-box configurations often include one or more weak points such as:
i. An administrative account with a pre-set, publicly known default password or without multifactor authentication enabled.
ii. Pre-enabled but unnecessary user accounts (sometimes with special access privileges).
iii. Pre-installed but unnecessary applications or services.
These default installations can allow attackers to gain unauthorised access to the organisation’s sensitive information. Therefore, the organisation will apply technical controls when installing computers and network devices, to minimise vulnerabilities and protect against common types of attack.
The organisation will manage all computers and network devices by:
a. Removing and disabling unnecessary user accounts (such as guest accounts and administrative accounts that will not be used).
b. Changing any default or guessable account passwords (see ‘Password-based Authentication’).
c. Removing or disabling unnecessary software (including applications, system utilities and network services).
d. Disabling any auto-run feature which allows file execution without user authorisation (e.g. when they are downloaded).
e. Ensuring users are authenticated before allowing them access to organisational data or services.
f. Ensuring appropriate device locking controls (see ‘device unlocking’ below) for users that are physically present.
If a device requires a user’s physical presence to access a device’s services (such as logging on to a laptop or unlocking a mobile phone), a credential such as a biometric, password or PIN will be in place before a user can gain access to the services.
The organisation will protect the chosen authentication method chosen (e.g. biometric authentication, password or PIN) against brute-force attacks.
Where it is possible to configure within the software, the organisation will apply one of the following depending on the functionality:
1. ‘Throttling’ the rate of attempts, so that the number of times the user must wait between attempts increases with each unsuccessful attempt. You should not allow more than 10 guesses in five minutes.
2. Locking devices after more than 10 unsuccessful attempts.
When the software is provided by a third party, and the vendor does not allow configuration of the above, we will use the vendor’s default setting.
Technical controls will be used to manage the quality of credentials. Where credentials are used to unlock a device, we will use a minimum password or PIN length of at least six characters.
When the device unlocking credentials are also used for authentication, we will apply the full password requirements to the credentials described in the section below for ‘user access controls.’
Security update management is applicable to servers, desktop computers, laptops, tablets, mobile phones, firewalls, routers, IaaS, PaaS and SaaS.
The organisation aims to ensure that devices and software are not vulnerable to known security issues for which fixes are available.
Any device that runs software can contain security flaws, known as vulnerabilities. Vulnerabilities are regularly discovered in all types of software.
Once discovered, malicious individuals or groups often move quickly to misuse (or ‘exploit’) vulnerabilities to attack computers and networks.
It is important to note that software vendors provide fixes for vulnerabilities identified in products that they still support, in the form of software updates known as ‘patches’ or security updates.
These may be made available to customers immediately or on a regular release schedule, e.g. monthly.
As an organisation we will make sure that all software is kept up to date and will:
i. Be licensed and supported.
ii. Removed from devices when it becomes unsupported or removed from scope by using a defined subset that prevents all traffic to/from the internet.
iii. Have automatic updates enabled where possible.
iv. Be updated, including applying any manual configuration changes required to make the update effective, within 14 days of an update being released, where:
v. The update fixes vulnerabilities described by the vendor as ‘critical’ or ‘high risk.’
The update addresses vulnerabilities with a Common Vulnerability Scoring System (CVSS) v3 base score of 7 or above.
vi. There are no details of the level of vulnerabilities the update fixes provided by the vendor.
For optimum security it is advised by Cyber Essentials that all released updates are applied within 14 days of release (this is not mandatory). It is important that updates are applied as soon as possible, and 14 days is considered a reasonable period. Any longer would constitute a serious security risk while a shorter period may not be practical. Some vendors release security updates for multiple issues with differing severity levels as a single update. If such an update covers any ‘critical’ or ‘high risk’ issues then it should be installed within 14 days.
Sometimes the vendor will use different terms to describe the severity of vulnerabilities, see the precise definition in the Common Vulnerability Scoring System (CVSS) (https://www.balbix.com/insights/understanding-cvss-scores/).
For the purposes of the Cyber Essentials scheme, ‘critical’ or ‘high risk’ vulnerabilities are those with a CVSS3 score of 7 or above or are identified by the vendor as ‘critical or high risk.’
User access controls are applicable to all servers, desktop computers, laptops, tablets, mobile phones, IaaS, PaaS and SaaS.
The organisation uses user access controls to ensure that user accounts:
1. Are assigned to authorised individuals only.
2. Provide access to only those applications, computers and networks the user needs to carry out their role.
Every active user account in the organisation facilitates access to devices and applications, and to sensitive business, and potentially personal, information. Only authorised individuals will be assigned access to user accounts and will only be granted as much access as they need to carry out their role. This supports the organisation in reducing the risk of information being stolen or damaged or breaches of confidential information.
Compared to normal user accounts, accounts with special access privileges have enhanced access to devices, applications and information, e.g. IT administrators. If these accounts are compromised, an attacker could take advantage of the greater accesses to corrupt information on a large scale, disrupt business processes, access personal data or gain unauthorised access to other devices in the organisation.
Administrative accounts are especially highly privileged, for example. These accounts typically allow the user to:
i. Execute software that can make significant and security-related changes to the operating system.
ii. Make changes to the operating system for some or all users.
iii. Create new accounts and allocate privileges.
All administrators will have this kind of account, including domain administrators and local administrators. This is important because if a user opens a malicious URL or email attachment, the malware would typically be executed with the same privilege level of the user’s account.
This is why the organisation will take special care allocating and using privileged accounts.
The organisation will control all user accounts, especially those with access privileges that allow access to your organisational data and services. This also includes third party accounts, e.g. accounts used by support services.
The organisation will:
1. Have in place a process to create and approve user accounts.
2. Authenticate users with unique credentials before granting access to applications or devices (see‘Password-based Authentication’).
3. Remove or disable user accounts when they are no longer required (e.g. when a user leaves the organisation or after a defined period of account inactivity).
4. Implement MFA, where available.
5. Authentication to cloud services will always use MFA.
6. Use separate accounts to perform administrative activities only (no emailing, web browsing or other standard user activities that may expose administrative privileges to avoidable risks).
7. Remove or disable special access privileges when no longer required (e.g. when a member of staff changes role).
All user accounts require the user to authenticate and where this is carried out using a password, the organisation will put in place the following protective measures:
1. Passwords are protected against brute-force password guessing by implementing at least one of the following:
2. Multi-factor authentication (see below).
3. ‘Throttling’ the rate of attempts, so that the number of times the user must wait between attempts increases with each unsuccessful attempt. The organisation will not allow more than 10 guesses in five minutes.
4. Locking devices after no more than 10 unsuccessful attempts.
5. Use technical controls to manage the quality of passwords. This will include one of the following:
6. Using multi-factor authentication (see below).
7. A minimum password length of at least 12 characters, with no maximum length restrictions.
8. A minimum password length of at least eight characters, with no maximum length restrictions and use automatic blocking of common passwords using a deny list.
9. We will aim to support users to choose unique passwords for their work accounts by:
10. Educating people about avoiding common passwords, such as a pet’s name, common keyboard patterns or passwords they have used elsewhere. This could include teaching people to use the password generator feature built into some password managers.
11. Encouraging people to choose longer passwords by promoting the use of multiple words (a minimum of three) to create a password (such as the NCSC’s guidance on using three random words (https://www.ncsc.gov.uk/collection/top-tips-for-staying-secure-online/three-random-words)).
12. Providing usable secure storage for passwords (e.g. a password manager or secure locked cabinet) with clear information about how and when it can be used.
13. Not enforcing password complexity requirements.
The Data Security and Protection Lead or the Registered Manager will ensure that passwords will be promptly changed where it is known or suspected a password or account has been compromised.
As well as providing an extra layer of security for passwords that are not protected by the other technical controls, the organisation will use multi-factor authentication to give administrative accounts and accounts that are accessible from the internet extra security.
The password element of the multi-factor authentication approach will have a password length of at least eight characters, with no maximum length restrictions.
There are four types of additional factor which will be considered:
i. A managed/enterprise device
ii. An app on a trusted device
iii. A physically separate token
iv. A known or trusted account
Additional factors may be chosen so that they are usable and accessible.
For more information see
‘NCSC’s guidance on MFA (https://www.ncsc.gov.uk/guidance/multi-factor-authentication-online-services).’
Malware protection applies to all servers, desktop computers, laptops, tablets, mobile phones, IaaS, PaaS and SaaS.
The organisation’s aim is to restrict execution of known malware and untrusted software, from causing damage or accessing data within the company’s IT systems and networks.
Malware, such as computer viruses, worms and ransomware, is software that has been written and distributed deliberately to perform malicious actions. Potential sources include malicious email attachments, downloads (including those from application stores), and direct installation of unauthorised software.
Infected systems within the organisation are likely to suffer from problems like malfunctioning systems, data loss, or onward infection that goes unseen until it causes harm elsewhere or across the whole network.
The organisation will aim to avoid the potential for harm by:
i. Preventing malware from being delivered to devices
ii. Preventing malware from running on devices
The organisation will ensure that a malware protection mechanism is active on all devices.
For each device, the organisation will use at least one of the options listed below, either using built in features in the software supplied or by purchasing products from a third-party provider.
In all cases the anti-malware software will be active, kept up to date in accordance with the vendor’s instructions, and configured to work as detailed below:
Where we use anti-malware software to protect devices it will be configured to:
1. Be updated in line with vendor recommendations
2. Prevent malware from running
3. Prevent the execution of malicious code
4. Prevent connections to malicious websites over the internet
5. The devices will be configured to only allow approved applications, which are restricted by code signing, execute on devices.
We will:
a. Actively approve such applications before deploying them to devices.
b. Maintain a current list of approved applications, users must not be able to install any application that is unsigned or has an invalid signature.
Backing up means creating a copy of your information and saving it to another device or to cloud storage (online).
Backing up regularly means the organisation will always have a recent version of important and business critical information saved. This will help the organisation to recover quicker if your data is lost or stolen. Where available the organisation will turn on automatic backup to regularly save information into cloud storage, without you having to remember.
Where we back up information to a USB stick or an external hard drive, it will be disconnected it from computers or networks when a backup is not being done.
Backing up data is not a technical requirement of Cyber Essentials, however it is highly recommended as part of business continuity planning.
Data Security and Protection Toolkit (https://www.dsptoolkit.nhs.uk/)
Data security: local support, national webinar and film series, Digital Care Hub
(https://www.digitalcarehub.co.uk/data-security-local-support-national-webinar-and-film-series/)
Digital and data-driven health and care technology, A guide to good practice for the use of digital technology in health and care
(https://www.gov.uk/government/publications/code-of-conduct-for-data-driven-health-and-care-technology)
NCSC’s guidance on MFA (https://www.ncsc.gov.uk/guidance/multi-factor-authentication-online-services)
NCSC’s guidance on using three random words
(https://www.ncsc.gov.uk/collection/top-tips-for-staying-secure-online/three-random-words)
Common Vulnerability Scoring System (CVSS)
(https://www.balbix.com/insights/understanding-cvss-scores/)
Updates to the Cyber Essentials Scheme (https://www.gov.uk/government/publications/ppn-0923-updates-to-the-cyber-essentials-scheme)
Cyber Essentials: Requirements for IT infrastructure v3.1(https://www.ncsc.gov.uk/files/Cyber-Essentials-Requirements-for-Infrastructure-v3-1-January-2023.pdf)
Quality Statements
We have a proactive and positive culture of safety based on openness and honesty, in which concerns about safety are listened to, safety events are investigated and reported thoroughly, and lessons are learned to continually identify and embed good practices.
We work with people to understand what being safe means to them as well as with our partners on the best way to achieve this. We concentrate on improving people’s lives while protecting their right to live in safety, free from bullying, harassment, abuse, discrimination, avoidable harm and neglect. We make sure we share concerns quickly and appropriately.
We detect and control potential risks in the care environment. We make sure that the equipment, facilities and technology support the delivery of safe care.
We make sure there are enough qualified, skilled and experienced people, who receive effective support, supervision and development. They work together effectively to provide safe care that meets people’s individual needs.
We tell people about their rights around consent and respect these when we deliver person-centred care and treatment.
We always treat people with kindness, empathy and compassion and we respect their privacy and dignity. We treat colleagues from other organisations with kindness and respect.
We provide appropriate, accurate and up-to-date information in formats that we tailor to individual needs.
We have a shared vision, strategy and culture. This is based on transparency, equity, equality and human rights, diversity and inclusion, engagement, and understanding challenges and the needs of people and our communities in order to meet these.
We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.
Key questions and quality statements – Care Quality Commission (https://www.cqc.org.uk/assessment/quality-statements)
Spot check that staff understand their responsibility towards data security
Spot check that staff are aware of our data protection policies
Have staff received training on data protection?
Have any staff undergone disciplinary action in relation to data protection and security?
Spot check that staff understand how to report security breaches and near misses.
Physical Access to Hardcopy Records
Check the record of which staff have access to confidential areas is up to date.
All offices, files, or cabinets which contain confidential information are kept locked when not in use.
Has all confidential waste been disposed of securely and are there destruction certificates? (If applicable)
Has anyone inappropriately accessed, or attempted to access, confidential records?
Digital Access to Records
Is the allocation of administrator rights restricted?
Have staff access rights been reviewed?
Check if there is any evidence of staff sharing access rights.
Screens are locked when not in use.
Check that our password policy is being followed
Has anyone inappropriately accessed, or attempted to access, confidential records?
Have appropriate security measures been applied to all computers, laptops and mobile devices?
Staff are using computers appropriately, e.g. no personal use, no downloading unapproved software, no social media use etc.
Sharing Data
Our procedures for safely sharing personal information via post are being followed.
Our procedures for safely sharing personal information via fax are being followed.
Our procedures for safely sharing personal information via secure email are being followed.
Legal Checks
The Information Asset Register has been reviewed and signed off.
The Record of Processing Activities has been reviewed and signed off.
Records of consent are up to date and still applicable.
Health and Social Care Act 2008 (Regulated Activities) Regulations 2014 [17]
Learning culture
Safeguarding
Safe environments
Safe and effective staffing
Consent to care and treatment
Kindness, compassion and dignity
Providing information
Shared direction and culture
Governance, management and sustainability
Please see the ‘Quality Statements’ section for full guidance
The National Data Opt-Out (https://digital.nhs.uk/services/national-data-opt-out) was introduced on 25 May 2018, to enable NHS patients to opt out from the use of their data for research or planning purposes, in line with the recommendations of the National Data Guardian (NDG).
The national data opt-out implements the opt-out model proposed by the National Data Guardian, as accepted by the Government and directed by the Department of Health and Social Care. The National Data Opt-Out applies to all publically funded health and social care.
This policy and procedure are provided for the regulated activity of personal care.
Our organisation is committed to equal rights and the promotion of choice, person-centred care and independence. This policy demonstrates our commitment to creating a positive culture of respect for all individuals. The intention is, as required by the Equality Act 2010, to identify, remove or minimise discriminatory practice in the nine named protected characteristics of age, disability, sex, gender reassignment, pregnancy and maternity, race, sexual orientation, religion or belief, and marriage and civil partnership. It is also intended to reflect the Human Rights Act 1998 to promote positive practice and value the diversity of all individuals.
1. The National Data Opt-Out was introduced on 25th May 2018, and the deadline for compliance was the 31st July 2022.
2. The national data opt-out implements the opt-out model proposed by the National Data Guardian, as accepted by the Government and directed by the Department of Health and Social Care.
3. The organisation will comply with the Data Protection Act 2018 and General Data Protection Regulations (UK GDPR), including Article 5 – Principles and Article 6 – Lawful Bases for Processing Data, for both public and privately funded delivery of the regulated activity.
4. It is this organisation’s aim to support service users in exercising their right to opt out and to ensure that their data is managed securely in line with all relevant guidance, legislation and regulation including:
5. Data Protection Act 2018 (DPA 2018)
6. UK General Data Protection Regulations (UK GDPR)
7. Code of practice on confidential information, NHS Digital
8.The Seven Caldicott Principles
9. Human Rights Act 1998
10. Common Law Requirement on Confidentiality (CLDC)
This is not an exclusive list and is provided for information and example.
It is the organisation’s aim to support service users in exercising their right to opt out and to ensure that their data is managed securely in line with all relevant guidance, legislation and regulations.
The organisation will comply with the Data Protection Act 2018 and General Data Protection Regulations (UK GDPR), including Article 5 – Principles and Article 6 – Lawful Bases for Processing Data, for both public and privately funded delivery of the regulated activity, i.e:
1. Consent: the individual has given clear consent for the organisation to process their personal data for a specific purpose.
2. Contract: the processing is necessary for a contract you have with the individual, or because they have asked you to take specific steps before entering into a contract.
3. Legal obligation: the processing is necessary for you to comply with the law (not including contractual obligations).
4. Vital interests: the processing is necessary to protect someone’s life.
5. Public task: the processing is necessary for you to perform a task in the public interest or for your official functions, and the task or function has a clear basis in law.
6.Legitimate interests: the processing is necessary for your legitimate interests or the legitimate interests of a third party, unless there is a good reason to protect the individual’s personal data which overrides those legitimate interests. (This cannot apply if you are a public authority processing data to perform your official tasks.)
The organisation will undertake a Data Protection Impact Assessment for each type and category of data being processed to ensure appropriate risk assessments and data management mitigation is in place.
It is our aim to support service users in exercising their right to opt out and to ensure that their data is managed securely in line with all relevant guidance, legislation and regulation including:
i. Data Protection Act 2018 (DPA 2018)
ii. UK General Data Protection Regulations (UK GDPR)
iii. Code of practice on confidential information, NHS Digital
iv. The Seven Caldicott Principles
v. Human Rights Act 1998
vi. Common Law Requirement on Confidentiality (CLDC)
This is not an exclusive list and is provided for information and example.
This is defined by the National Health Service Act 2006 (Section 251B) as information that meets all of the following three requirements:
1. Identifiable or likely identifiable (for example from other data likely to be in the possession of the data recipient), and
2. Given in circumstances where the individual is owed an obligation of confidence, and
3. Conveys some information about the physical or mental health or condition of an individual, a diagnosis of their condition; and/or their care or treatment.
It is important to note that this has been updated to ensure that the definitions used include local authority social care.
The term CPI includes special categories of personal data under Article 9 UK GDPR and also covers information about the deceased as the UK GDPR only applies to living individuals.
The following definition of individual (also called direct) care as set out in the National Data Guardian (NDG) Review is used to underpin the national data opt-out:
‘A clinical, social or public health activity concerned with the prevention, investigation and treatment of illness and the alleviation of suffering of individuals. It includes supporting individuals’ ability to function and improve their participation in life and society.
It includes the assurance of safe and high-quality care and treatment through local audit, the management of untoward or adverse incidents, person satisfaction including measurement of outcomes undertaken by one or more registered and regulated health or social care professionals and their team with whom the individual has a legitimate relationship for their care.’
The NDG review gave some further clarity on local clinical audit as follows:
‘The use of personal confidential data for local clinical audit is permissible within an organisation with the participation of a health and social care professional with a legitimate relationship to the patient through implied consent.
For audit across organisations, the use of personal confidential data is permissible where there is approval under Regulation 5 of the Health Service (Control of Patient Information) Regulations 2002.’
Section 251B and implied consent under CLDC will together provide the lawful basis to share in most cases of direct care. In these cases, and any cases of direct care based on explicit consent, the national data opt-out will not apply.
Indirect care includes:
1. Reviewing the care provided to ensure it is of the highest standard and quality.
2. Ensuring services meet patient needs in the future.
3. Investigating patient queries, complaints and legal claims.
4. Ensuring the hospital receives payment for the care received.
5. Preparing statistics on NHS performance.
6. Auditing NHS accounts and services.
7. Undertaking health research and development (with service users’ consent – you may choose whether or not to be involved).
8. Helping to train and educate healthcare professionals.
Nationally there are strict controls on how patient and service user information is used for these purposes. These decide whether information has to be de-identified first and with whom identifiable information can be shared.
The national data opt-out is a policy to be considered and applied with data protection legislation, other laws and best practice, including data protection legislation and the Common Law Duty of Confidentiality (CLDC), Human Rights Act 1998, and all relevant Codes of Practice of confidentiality and best practice guidance, e.g. the seven Caldicott Principles.
Data protection legislation requires the lawful basis for any processing to be communicated clearly to individuals through appropriate methods and materials in line with the duty of transparency.
The organisation will only manage and use a service user’s personal identifiable data for a lawful purpose, e.g:
1. For individual or direct care OR
2. Sharing with other health or social care providers providing care to the service user
In either case the opt-out does not apply.
Any other purpose beyond individual care will be assessed on a case-by-case basis, and data will be provided in an anonymised form where there is a contractual or legal requirement to provide the information where it does not directly pertain to the delivery of care.
The national data opt-out does not apply to information that is anonymised in line with the Information Commissioner’s Office (ICO) Code of Practice (CoP) on Anonymisation or is aggregate or count type data.
It does not apply to workforce or staff information, which is subject to UK GDPR and DPA 2018 protections.
A number of different channels are available for the public to set a national data opt-out. These are:
1. A digital (online) channel accessed via the national data opt-out service. National Data Opt-Out, NHS Digital (https://digital.nhs.uk/services/national-data-opt-out)
2. For those who need support to set their national data opt-out preference online a digitally- assisted channel is provided that enables members of the public to set a national data opt-out with assistance from NHS Digital staff via the national helpline.
3. NHS Digital Contact Centre phone number: 0300 303 5678 – Monday to Friday, 9am to 5pm (excluding bank holidays).
4. A non-digital (paper based) channel accessed by the national helpline or through forms which can be printed from the webpages
5. If they are a parent or legal guardian and they want to opt their children out, they must complete the opt-out form. Manage your choice, or your child’s choice on their behalf (https://assets.nhs.uk/prod/documents/Manage_your_childs_choice_on_their_behalf.pdf)
6. Once they have completed the form, they can email it to the Contact Centre at [email protected] (mailto:[email protected]) or via the NHS App (https://www.nhs.uk/nhs-services/online-services/nhs-app/)
There are some points that apply to specific groups with respect to setting a national data opt-out:
i. Individuals aged 13 or over are able to set a national data opt-out via the digital, digitally-assisted and non-digital channels.
ii. Those with parental responsibility (parents and legal guardians), are able to set a national data opt-out on behalf of a child under the age of 13 via the non-digital channel only.
iii. There is a specific form that allows a choice to be set for up to six children at once.
iv. Any national data opt-out that has been set by a person with parental responsibility for a child under the age of 13 will remain in place unless and until it is proactively changed.
v. Those who have a formal proxy relationship to make decisions on behalf of another adult (either a lasting power of attorney or a court appointed deputy) are able to set a national data opt-out on behalf of that person via the non-digital channel only.
vi. Individuals in the secure and detained estate (e.g. prisons) are able to set a national data opt-out through the healthcare professionals working in these settings.
vii. Individuals who have agreed with their GP for their records to be marked as sensitive will be offered the choice to set a national data opt-out through the established processes to set (or remove) a sensitive flag.
viii. A national data opt-out cannot be set for a deceased patient unless they have explicitly stated this in a last will or testament. This can only be done via the non-digital channel.
A national data opt-out is stored against a person’s individual record on the NHS Digital Spine against their NHS number.
Any person registered with an NHS number allocated to them is able to set a national data opt-out. This covers the majority of patients and service users who have received health or care services in England and, therefore, have data about them in the health and care system in England.
A child is able to set their own opt-out from age 13 which aligns with the minimum age at which children can give their consent to participate in digital services as set out in data protection legislation.
This is not based on any test of competence. Children under 13 and those who lack capacity are not able to set an opt-out themselves. In these cases, individuals who have a formal, legal relationship to act on behalf of them (i.e. somebody who has parental responsibility, a lasting power of attorney or court appointed deputy) are able to set an opt-out on their behalf by proxy.
The national data opt-out is defined based on purpose and applies to any disclosure of data for purposes other than individual or direct care.
Purposes other than individual care or direct care are defined as anything that does not meet the definition of individual care or direct care.
See ‘National Data opt-out, Appendix 2: Definitions (https://digital.nhs.uk/services/national-data-opt-out/operational-policy-guidance-document/appendix-2-definitions).’
It would include purposes such as planning for the provision of:
1. Local services
2. Managing and running NHS and adult social care services
3. Commissioning
4. Invoice validation
5. National clinical audits and research
The national data opt-out applies to data relating to publicly funded or arranged care only, i.e. by a local authority, ICB or NHS commissioner. This includes where the care is provided by a private provider and the service is fully or partially funded by the public body.
This is summarised as:
• All NHS organisations (including private patients treated within such organisations).
• Adult social care which is funded or arranged by a public body (typically a local authority).
• NHS arranged care within private providers (e.g. Nuffield, BMI Healthcare).
• Any release of data by NHS Digital which relates to private patients including that which is collected by a request under S259 of the Health and Social Care Act 2012 (HSCA).
• Privately (non-NHS) funded patients within private providers unless the care is funded or arranged by a public body.
• Care which is not provided or arranged by a public body, that is privately arranged/privately funded care.
It is of note that in adult social care, providers typically have a range of patients receiving both publicly funded and privately funded care in the same care service. The funding arrangements for individual service users may also change several times over short time periods. Under these circumstances:
• The organisation will review the best position for service users and may extend the national data opt-out to cover all the service users in order to make implementation within the service straightforward.
• In the case a voluntary extension is implemented, the organisation will make clear to services users, via contracts for the provision of care, privacy notices, and other provided information, the opportunity to opt out and the process.
Data controllers, whether solely or jointly with another organisation, are responsible for ensuring that national data opt-outs are applied in line with the ‘National Data Opt-Out Policy.’
In some cases this will require data controllers to instruct any organisations acting as a data processors under their instruction to apply the national data opt-out.
For our organisation it is most likely that the local authority, ICB or NHS commissioners who act as the data controllers will notify the service of the opt-out of the service user. The organisation, as the data processor, will then register within the services user’s care records the opt-out and comply with the notification related to sharing for the purposes of Indirect Care, including data for research or planning purposes.
Data controllers must apply national data opt-outs whenever confidential patient information is to be disclosed outside of their data controllership boundary in line with the wider policy (see ‘figure 1’ below) and is relying on section 251 support. Data controllers may also need to apply national data opt-outs for internal uses of the data where the purpose changes from individual care and the disclosure is relying on S.251 support to be lawful.
Further information on the responsibilities of data controllers is provided by the ICO (https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/controllers-and-processors/).
(https://www.igt.hscic.gov.uk/Resources/Data%20Controllers%20for%20shared%20records%20.pdf)
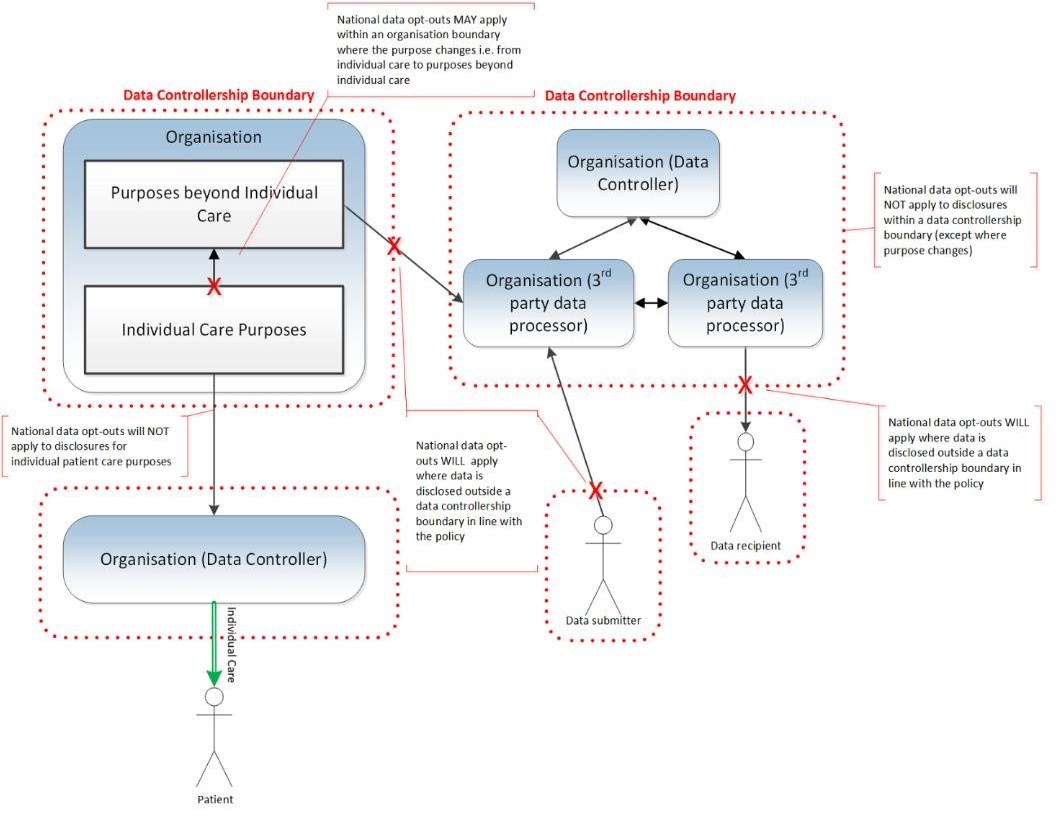
does the opt-out apply to? For the original diagram please see ‘Which organisation (https://digital.nhs.uk/services/national-data-opt-out/operational-policy-guidance-document/which-organisations-does-the-opt-out-apply-to)’
National data opt-out, NHS Digital (https://digital.nhs.uk/services/national-data-opt-out/national-data-opt-out-new)
Overview: Choose if data from your health records is shared for research and planning, NHS (https://www.nhs.uk/your-nhs-data-matters/)
National data opt-out, Digital SocialCare (https://www.digitalsocialcare.co.uk/national-dataoptout/#:~:text=Under%20the%20national%20data%20opt,or%20delivering%20their%20own%20care)
National Data opt-out; Appendix 2: Definitions, NHS Digital (https://digital.nhs.uk/services/national-data-opt-out/operational-policy-guidance-document/appendix-2-definitions)
Manage your choice, or your child’s choice on their behalf, NHS
(https://assets.nhs.uk/prod/documents/Manage_your_childs_choice_on_their_behalf.pdf)
Quality Statements
We have a proactive and positive culture of safety based on openness and honesty, in which concerns about safety are listened to, safety events are investigated and reported thoroughly, and lessons are learned to continually identify and embed good practices.
We work with people to understand what being safe means to them as well as with our partners on the best way to achieve this. We concentrate on improving people’s lives while protecting their right to live in safety, free from bullying, harassment, abuse, discrimination, avoidable harm and neglect. We make sure we share concerns quickly and appropriately.
We detect and control potential risks in the care environment. We make sure that the equipment, facilities and technology support the delivery of safe care.
We make sure there are enough qualified, skilled and experienced people, who receive effective support, supervision and development. They work together effectively to provide safe care that meets people’s individual needs.
We tell people about their rights around consent and respect these when we deliver person-centred care and treatment.
We always treat people with kindness, empathy and compassion and we respect their privacy and dignity. We treat colleagues from other organisations with kindness and respect.
We treat people as individuals and make sure their care, support and treatment meets their needs and preferences. We take account of their strengths, abilities, aspirations, culture and unique backgrounds and protected characteristics.
We promote people’s independence, so they know their rights and have choice and control over their own care, treatment and well-being.
We make sure people are at the centre of their care and treatment choices and we decide, in partnership with them, how to respond to any relevant changes in their needs.
We provide appropriate, accurate and up-to-date information in formats that we tailor to individual needs.
We have a shared vision, strategy and culture. This is based on transparency, equity, equality and human rights, diversity and inclusion, engagement, and understanding challenges and the needs of people and our communities in order to meet these.
We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.
Key questions and quality statements – Care Quality Commission (https://www.cqc.org.uk/assessment/quality-statements)

Keeping people safe is called Safeguarding.

Safeguarding means people are protected from abuse and neglect And
People live as independently as possible and make choices about
their lives.

Abuse is where someone does or says things that frighten you or cause you harm.

The Law says that we need to keep adults safe who are at risk of being abused.

Your rights
You have the right to live your life without being abused

An adult at risk of harm is:
• 18 years or older.
• Has care and support needs.
• This may be because of their age, disability, mental health needs, drug or alcohol misuse or other condition. And
• They are unable to protect themselves.
This could be you, friends, family members or other adults you know.
Abuse can happen anywhere.

At home

In a care or nursing home

In a hospital

At your work, day centre, college or social club

In a public place

On the internet or phone
There are different types of abuse.
Physical abuse is where someone hurts you.

It can be things like hitting, kicking, pushing, scratching, or biting.
It can also be if you are given the wrong medication, too much medication or not enough medication.

Touches your body or private parts where you do not want to be
touched or makes you touch them or their private parts.
Or makes you have sex or do a sexual thing that you do not want to.

Or shows you pictures or videos about sex that you don’t want to see.
Emotional abuse is also called psychological abuse.
It’s when someone does something or says something that makes
you feel bad or scared. It can be when someone who:

• Makes fun of you
• Bullies you or calls you names
• Threatens you, or makes you do things you don’t want to do
• Ignores you on purpose
• Treats you like a child
Financial abuse can include taking your belongings, money or benefits without your permission. It might be someone who:

• Steals your money
• Borrows your money or things and doesn’t give them back
• Makes you pay for things you don’t want to
• Changes your will
Neglect is when someone who is meant to help you, does not support you properly.
Neglect includes:

Not giving you choices or the things that you need like:
• Clean clothes
• Food
• The right medicine
• The right help
It also includes leaving you on your own for a long time when you
need support


Self–neglect is when you are not looking after yourself properly or
letting other people help you and this causes you harm.
Discrimination is when someone treats you differently or unfairly
because you are different to them.
People might treat you differently because of your:

• Race or religion
• Disability
• Age
• Gender
• Sexuality
Organisational abuse can be when you are not treated properly by people who are paid to support you. It can include:

• Staff make all the rules, and you don’t have choices
• Staff treat you badly and have a bad attitude
• Staff don’t know how to support you properly
• Not having a choice of what you want to do in your own home
Domestic abuse can be when your partner or a family member
hurts you in your home, makes you feel scared or forces you to
do something you don’t want to do.

Domestic abuse can include lots of the other types of abuse in this book including
• Physical abuse
• Emotional abuse
• Financial abuse

Modern Slavery is when someone forces you to work in a job that is against the law or does not pay you to work.
There are some other types of abuse you may not have heard of.
Hate Crime where someone hurts you or attacks you because of who you are.
This might be because of your race, disability, or something else.
Mate Crime where someone pretends to be your friend to take advantage of you.
This might be stealing your money, using your home, or eating your food.
Someone who abuses someone else could be anyone including:

• Your Parents
• Your staff
• Your friends
• Your college tutor
• A stranger
• Someone else
Remember that no one should ever abuse you and you have a right to be safe at all times.
Abuse and neglect is never ok.

If you think you are being abused
Tell someone you trust
This could be:

• A member of your family
• A friend
• A carer or support worker

• Your social worker
• An advocate
• The police

• A nurse or doctor
• An inspector from CQC
• Someone else you trust

Get in touch with us if you are worried about something



Or Phone the Local Authority Safeguarding Team.

Health and Social Care Act 2008 (Regulated Activities) Regulations 2014 [17]
Key Lines of Enquiry [S2.3, S2.4, C3.3, W2.3, W2.8, W5.2]
Safe systems, pathways and transitions
Safeguarding
Safe and effective staffing
Infection prevention and control
Medicines optimisation
Assessing need
How staff, teams and services work together
Consent to care and treatment
Kindness, compassion and dignity
Independence, choice and control
Person-centred care
Care provision, integration, and continuity
Providing information
Listening to and involving people
Planning for the future
Shared direction and culture
Capable, compassionate and inclusive leaders
Governance, management and sustainability
Please see the ‘Quality Statements’ section for full guidance
This policy details the safekeeping of all records from their creation to disposal. This includes our procedures for sharing information externally.
This policy includes in its scope all data which we process, either in hardcopy or digital copy; this includes special category data. This policy applies to all staff, including temporary staff and contractors.
When we create records, we use standardised structures and layouts for the contents of records. All records are kept in accessible but protected locations. The location of these records is documented in the Information Asset Register (IAR). Template provided at: Digital Social Care Information Asset Register
(https://www.digitalsocialcare.co.uk/resource/information-asset-register-template/)
This policy and procedure are provided for the regulated activity of personal care.
Our organisation is committed to equal rights and the promotion of choice, person centred care and independence. This policy demonstrates our commitment to creating a positive culture of respect for all individuals. The intention is, as required by the Equality Act 2010, to identify, remove or minimise discriminatory practice in the nine named protected characteristics of age, disability, sex, gender reassignment, pregnancy and maternity, race, sexual orientation, religion or belief, and marriage and civil partnership. It is also intended to reflect the Human Rights Act 1998 to promote positive practice and value the diversity of all individuals.
• Both service users and staff records are properly created, accessible and available for use and they are disposed of in a secure and timely fashion.
• Throughout the lifespan of the record, we ensure documentation reflects the continuum of care and is in chronological order.
• In line with legislation, personal information is not processed without a lawful basis being identified.
• Guidelines for staff on the secure use of personal information are outlined here.
• Staff members have been provided with training on verbal communications.
This policy will ensure that service users and staff records are properly created, accessible and available for use and that they are disposed of in a secure and timely fashion in line with the Records Management Code of Practice for Health and Social Care 2016. It provides staff with guidance regarding individual responsibility for accuracy and appropriate storage of records.
The organisation recognises the sensitive and private nature of the information it gathers to be able to deliver its services as a provider of regulated activities. It is the organisations aim to train and support staff to be competent and comply with the relevant legislation and regulations, including the Data Protection Act 2018, General Data Protection Regulations (GDPR) and the Records Management Code of Practice for Health and Social Care 2016.
This Record Keeping Policy covers:
• Record keeping
• Managing records
• Transparency procedures
• Our retention and disposal procedures
• Our information handling procedures, including our procedures for safely and legally sharing information
• Procedures for individual making requests about their data (GDPR individual data rights)
• Subject Access Request procedures
• Right to erasure (‘Right to be forgotten’) procedures
• Right to restrict processing procedures
• Right to object procedures
• Our procedures when there is a withdrawal of consent to share
As a provider of a Regulated Activity under the Health and Social Care Act 2008 (Regulated Activities) Regulations 2014, the organisation has legitimate and necessary reasons for recording and holding personal and special category information relating to both service users and staff under the GDPR and the Data Protection Act 2018.
The organisation seeks consent from service users to hold the following information (provided as an example and not exhaustive):
• Care Assessment and Care and Support Plans.
• Medication, including time and dosage.
• Details of health and social care professionals who support them.
• Financial information to support the service user daily life e.g. shopping.
• Recording and communicating changes in the service user’s or carer’s circumstances, health, physical condition, or care needs.
• Any accident, however minor, to the service user and/or care or support worker.
• Safeguarding incidents.
The organisation and its staff will:
• Maintain up-to-date and accurate records.
• Provide service users with access to their records and information.
• Provide opportunities for service users to confirm their personal records are accurate and factual at initial assessment and care reviews.
• Ensure that all files or written information of a confidential nature are stored in a secure manner in a locked filing cabinet and are only accessed by staff who have a need and a right to access them.
• Ensure that all files or written information of a confidential nature are not left in a place where they can be read by unauthorised staff or others.
• Check regularly on the accuracy of data being entered into computers.
• Always use the passwords provided by the organisation to access the computer system and not abuse them by passing them on to people who should not have them.
• Use computer screen blanking or screen savers to ensure that personal data is not left on screen including:
• Service users
• Personnel data
• Interview/recruitment records
• Complaints
• Accounts and financial transactions
All personal records and organisation records are kept securely; in good order; and are constructed, maintained and used in accordance with data protection legislation and other statutory requirements.
The organisation believes that access to information, and security and privacy of data, is an absolute right of every service user and staff member.
In addition, the organisation believes that service users are entitled to see a copy of all personal information held about them, and to correct any error or omission therein.
The organisation will share information where there is a need to protect, safeguard and support health and wellbeing of the service user or carer, and where it would be more harmful not to share information. Staff and the organisation will work in the best interests of the service user, and will share information in line with the Data Protection Act 2018 Code of Practice.
Please refer to the Safeguarding Adults Policy and the Confidentiality Policy.
Throughout the lifespan of the service users and staff records, we ensure documentation is accurate, contains only relevant personal information, factual, in black ink, timed & dated, and is contemporaneous in line with legal and guidance requirements. (i.e. contemporaneous notes are, wherever possible, taken at the time of meetings, episodes of care, telephone calls, visits to premises).
We provide clearly written documentation to support the safe delivery of care and support to service users including:
• Care Assessment
• Risk Assessments
• Care and Support Plan
• Care Notes
• Care Review
The organisation ensures records are maintained, updated and shared with those who have a legal basis for accessing the information. We provide staff with guidance and training on the creation and use of records and their legal responsibilities to share and safeguard personal confidential information.
At any point in the lifespan of the record, the data subject can ask for a Subject Access Request (SAR), as detailed below:
• The data subject has the right to request access to their data.
• The data subject has the right to request that their record is corrected.
• The data subject has the right to request the erasure (‘right to be forgotten’) of their record. The request to erasure does not apply in the following circumstances:
• Where the organisation requires the data to comply with a legal obligation;
• (With reference to special category data) for the provision of health or social care; or
• For the management of health or social care systems or services.
The organisation will:
• Only retain records while they are necessary for the purposes for which they were originally collected. We will ensure that all records are retained and destroyed in line with the records management code of practice for health and social care 2016.
• At least annually we guarantee that we will audit our record keeping procedures.
• Implement and follow the DPA principles:
• Personal information must be fairly and lawfully processed.
• Personal information must be processed for limited purposes.
• Personal information must be adequate, relevant and not excessive.
• Personal information must be accurate and up to date.
• Personal information must not be kept for longer than is necessary.
• Personal information must be processed in line with the data subjects’ rights.
• Personal information must be secure.
• Personal information must not be transferred to other countries without adequate protection.
Our privacy notice outlines to people why we hold their data, the lawful basis for doing so, and their rights in terms of how we process their data.
Our privacy notice is freely available to all individuals whose data we process and is part of our commitment to transparency and accountability. It satisfies the individual’s right to be informed under GDPR.
Our privacy notice can be found:
All service users, or their legal representative, will be informed of their rights regarding their personal data when they sign their care and support contract.
The privacy notice will be reviewed and updated at least annually.
We will provide people with this information when we request their personal data.
If we receive an individual’s personal data from a source other than that individual, we will provide them with privacy information without undue delay and at least within one month.
We will adhere to the retention timelines determined by the Information Governance Alliance (IGA) in Appendix 3 of Records Management Code of Practice for Health and Social Care 2021 (https://www.gov.uk/government/publications/records-management-code-of-practice-for-health-and-social-care).
At the end of their lifespan, the records will go through an appraisal process. This process will determine if there is a continuing legal basis for keeping the record. Alison Bullous will have final responsibility for determining whether the record will be destroyed or retained. They will maintain a record of all retention or disposal decisions.
In the instance that records are destroyed, our in-house process is the process begins with identifying which records are no longer needed and determining the appropriate method of destruction. Secure shredders are fitted in each office and are utilised for physical documents, ensuring complete destruction of sensitive information. A documented record of the destruction process is maintained to demonstrate compliance with data protection regulations.
Our processes meet the British Security Industry Association (https://www.bsia.co.uk/publications/information-destruction/) EN 15713:2009 standard by:
Where the organisation uses a third-party contractor to dispose of records, it has in place a written contract which specifies that their compliance with the standard. They are also contracted to provide disposal certificates which are kept in line with our records.
Additional support and guidance can be found at Digital Social Care – Advice on Contracts for Secure Disposal of Personal Data (https://www.digitalsocialcare.co.uk/resource/advice-on-contracts-for-secure-disposal-of-personal-data/)
Information handling procedures ensure that personal information is protected and that it is not disclosed inappropriately, either by accident or design, whilst in use or when it is being transferred.
In line with legislation, personal information is not processed without a lawful basis being identified. The Record of Processing Activities (ROPA) records all processing of personal data and identifies the legal basis for it being processed.
Record of Processing Activities information, guidance and template is provided below by Information Commissioner’s Office (ICO):
ICO: Guide to data protection (https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/documentation/how-do-we-document-our-processing-activities/#how5)
The ROPA template, or similar, will be completed and reviewed annually (or as services are changed/updated) to ensure that the Processing Activities are up to date and identifies the legal basis for processing the data.
These procedures cover all records which contain data or information which can be said to contain sensitive, commercialor personal data whether stored in hardcopy or digitally.
We ensure that there are secure points for the receipt of personal information transferred to us and we have applied the following measures to safeguard personal information during receipt and transfer/transit:
Emails containing sensitive data are encrypted to ensure secure transmission. We actively discourage the use of USB or external hard drives for data transfer due to security risks. Employees are trained on proper data handling procedures, including using encrypted email services and avoiding unsecured storage devices. These measures uphold confidentiality and compliance with data protection regulations.
Staff members have received training on verbal communications. They know that they must take appropriate precautions not to reveal confidential information e.g. to avoid being overheard when making a phone call or not to have confidential conversations in public places or open offices. The staff handbook and staff training inform employees that breach of this procedure may be a disciplinary or legal offence.
We will ensure that all confidential information we transfer by post or courier is done so as securely as is practicable. All records transferred in this manner are addressed to a named individual and marked “Private and Confidential”. All records which are posted will be done through Signed-for delivery so that it is guaranteed that the correct person receives the record.
Portable devices provide both an opportunity and a risk to the delivery of care and support, especially the management of information and data.
Portable devices have inherent risks of being misplaced, stolen or accessed inappropriately e.g. when left unattended. We recognise that information held on portable devices is at increased risk. Portable devices include memory sticks, CDs, DVDs, mobile phones and laptops.
Where portable devices are provided by the organisation these are documented on the Information Asset Register, and all relevant staff have received guidelines on safe usage and have signed a Portable Device Assignment Form.
Due to the increased risk of viruses and the risk of losing data, staff are prohibited, unless they have express permission from the Registered Manager, to use or connect to the organisations computers personal:
• Memory sticks
• CDs/DVDs
• Mobile phones
• Laptops
Mobile phones, laptops, memory sticks and other relevant devices provided by the organisation will be encrypted and password protected to ensure personal data on the device is protected.
These devices will be managed by the organisations IT department, who will be responsible for ensuring they are up to date with:
• Security updates e.g. Windows
• Virus protection
• Passwords in line with company policy
• Encryption software
• Organisation required applications e.g. Care Management Software
• Equipment specification
In addition, staff are prohibited, where they are provided equipment by the organisation, to connect it to their personal computers or equipment.
• Portable devices such as memory sticks, CDs, etc. must not be used on personal computers.
• All portable devices are security marked with barcode and company sticker.
• Password protected screensavers are installed on laptops.
• Anti-virus software is in use and is regularly updated.
• Regular backups are taken of the data stored on portable devices.
• All portable devices are protected by either a PIN or password (dependent on the type of device).
Bring Your Own Devices (BYOD) Policy will be required where there is extensive use of employee-owned mobile phones. Guidance on what this policy might include is available here:
• ICO – Cyber Security, bring your own device (BYOD) (https://www.digital.nhs.uk/cyber-security/policy-and-good-practice-in-health-care/bring-your-own-device)
Please also be aware that if personal phones are to be used by employees and charged up in work time, then the plug and cable will be subject to PAT (Portable Appliance Testing).
Where the company asks staff to use their own phones at work this may include the following methods of work:
At this level no personal information will be held on their phones related to service users or staff (unless staff have given permission to the person to have that information e.g. mobile numbers)
All data accessed will be via a cloud-based system, with password protected access to the organisations data and information. Once the staff member has logged out then no data (unless files have been saved e.g. rosters) will remain on the phone or mobile device.
All data accessed will be via a cloud-based system, with password protected access to the service users data via a dedicated application. Applications will be automatically and remotely deleted or passwords revoked when staff leave the organisation.
Once the staff member has logged out then no data will remain on the phone or mobile device, with no provision to copy or save information to the phone or mobile device.
See guidance Digital Social Care (https://www.digitalsocialcare.co.uk/social-caretechnology/mobile-devices/guide-to-smartphones-and-mobile-devices-in-social-care-providing-company-phones-or-bring-your-own/level-three-core-functions-and-operational-care/)
Fax machines have been banned in the NHS by the Health and Social Care Secretary as of April 2020.This organisation will not use Fax for the transfer of personal or special category information.
Confidential information must never be sent via external email, either as part of the message or attached as a Word, Excel or other document, which contains personal information about service users or staff, unless the email is encrypted at both ends of the communication or is password protected using an agreed standard. Emails sent to and from health and social care organisations must meet the secure email standard (DCB1596) so that everyone can be sure that sensitive and confidential information is kept secure. You can find out more about the standard, and the action you must take at “The secure email standard (https://digital.nhs.uk/services/nhsmail/the-secure-email-standard#top)”, NHS Digital.
The Data Security and Protection Toolkit is an online self-assessment tool that allows organisations to measure their performance against the National Data Guardian’s 10 data security standards.
All organisations that have access to NHS patient data and systems must use this toolkit to provide assurance that they are practising good data security and that personal information is handled correctly. You can find out more about the toolkit at “Data Security and Protection Toolkit (https://www.dsptoolkit.nhs.uk/)”, NHS Digital.
Care should be taken to practice good data security when transmitting personal, sensitive or confidential information. If you are unsure you should check if the recipients email address is secure and that they know the nature of the information being transmitted.
Digital Social Care work in partnership with NHS Digital to support adult social care providers to support their digital transformation. They have a range of free supported resources and guidance which can be accessed at
Digital Social Care (https://www.digitalsocialcare.co.uk/).
No person identifiable information will be sent via text or social media or other public platform or forum.
GDPR provides all individuals specific rights when it comes to their personal data.
To exercise these rights an individual should contact any staff member, through the Data Protection Champion, or equivalent job role, to make a request, either verbally or in writing.
In the instance that the request is made to a member of staff who is not the Data Protection Champion or equivalent job role, that staff member will inform the Data Protection Champion or Registered Manager as soon as possible. The timeline for responding to requests begins from when the first staff member is contacted.
In all cases we will respond to a request without delay and in a timeframe not exceeding one month from when the request was made.
Should the request be complex this may be extended to two months; we will inform the individual in writing of the extension, and the reasons why it is required, within one month.
If the request is manifestly unfounded, or excessive, we may either request a reasonable fee to cover our administrative costs or we may refuse to comply with the request.
If we refuse to comply with a request, we will inform the individual why we are not taking action, tell them about their right to complain to the ICO, and tell them that they have the right to seek a judicial remedy.
In order to process any request, we will use reasonable means to verify the identity of the individual making the request so that no data is shared inappropriately.
The Data Protection Champion, or equivalent job role, will maintain a log of all requests and their outcomes.
All staff will be informed of these procedures in the staff handbook.
All individuals have the right to access their personal data which we process and store. Confidential records of the deceased have the rights afforded to them by the Duty of Confidentiality and the Access to Health Records Act 1990.Should any person wish to request access for any records of the deceased they should contact the Data ProtectionChampion, or equivalent job role.
We will provide a copy of any information which it is lawful to provide free of charge. If further copies are required, we will charge a fee which will exclusively cover the administration costs of making copies.
We will provide copies of the information requested in a reasonable format, either hard copy or digital.
All people have the right to request the erasure of their data which we control or process. People can request for their data to be erased in the following instances:
• Where the personal data is no longer necessary in relation to the purpose for which it was originally collected/processed
• When they withdraw consent
• When they object to the processing and there is no overriding legitimate interest for continuing the processing
• If the personal data was unlawfully processed
• If the personal data must be erased in order to comply with a legal obligation
We will not be able to honour any requests to have personal data erased when the data is being processed for the following reasons:
• To assess the working capacity of an employee
• To provide a medical diagnosis
• To provide health or social care or treatment or the management of health or social care systems and services
• To exercise the right of freedom of expression and information
• To comply with a legal obligation for the performance of a public interest task or exercise of official authority
• For public health purposes in the public interest
• Archiving purposes in the public interest, scientific research historical research or statistical purposes
• The exercise or defence of legal claims
Where at all possible, in the instance that we have appropriately shared an individual’s records with any third party, we will inform this third party of the erasure if appropriate.
We will erase records in line with the disposal procedures set out above.
Right to Restrict Processing Procedures
All individuals have the right to request that we restrict the processing of their data in the following circumstances:
• While we are verifying the accuracy of any data we keep when an individual has made a request for the rectification of their personal data
• In the instance that their personal data has been processed unlawfully and the individual requests that their data is not erased
• When we do not need to keep the personal data, but the individual has requested that we keep it in order to establish, exercise or defend a legal claim
If an individual objects to us processing their personal data, we will restrict all processing while we investigate the request. When we restrict processing, we will store the individual’s personal data but will not process their data in any other way.
The organisation will establish a process for how it demonstrates that it is not processing data under these circumstances. For example, moving a paper file into a separate secure location so that it can only be accessed by appropriate people or, if it is a digital record, temporarily make the data inaccessible to users. The organisation will demonstrate that it has restricted processing in place.
All people have the right to object to us processing their data in certain circumstances, and have the absolute right to object to the organisation using their personal data for any direct marketing.
The organisation will not use service user or staff personal data for marketing purposes without their written and express permission.
If subsequently they withdraw consent and they object to us using their data for marketing, we will immediately stop using their data for this purpose. We will retain only enough data so that their request can be respected.
Individuals can also object to us processing their data if we are doing it under Public Task or Legitimate Interests grounds.
The individual should provide specific reasons for why they object.
We cannot comply with the objection if we have compelling legitimate grounds for the processing which override the interests, rights and freedoms of the individual, or if the processing is for the establishment, exercise or defence of legal claims.
In the instance that we cannot comply we will clearly document our decision for this, inform the individual and inform them of their right to go to the ICO or to seek judicial recourse.
All people have the right to withdraw their consent to have their personal information shared at any time. We guarantee that it will be as easy to withdraw consent as it is to give consent.
If an individual withdraws their consent to share information, we will discuss this and explain how this decision may impact on their health and care outcomes.
In certain instances, where legislation or public good outweighs the individual’s right to not consent to information sharing, we may not be able to honour any withdrawal of consent. This will be discussed and will only occur if we can demonstrate compelling legitimate grounds for the processing which override the interests, rights and freedoms of the individual.
Any time in which consent is not given, or is withdrawn, the Data Protection Champion, or equivalent job role, will keep a log of this and a note will be made on the individual’s records.
The Data Protection Champion is responsible for maintaining records around Subject Access, Rectification, Erasure and Withdrawal of Consent requests.
The Data Protection Champion is also responsible for maintaining staff training on record keeping and auditing staff knowledge annually.
The Data Protection Champion will report to the Senior Information Risk Owner (SIRO) any Subject Access Requests or similar.
If appropriate, The Data Protection Officer has final say on any Subject Access decisions.
The SIRO will monitor compliance with the Record Keeping Policy and has responsibility for reviewing the policy at least annually.
Please note this document has been modified from the Digital Social Care (https://www.digitalsocialcare.co.uk/latest-guidance/template-policies/) Record Keeping Policy Template. (https://www.digitalsocialcare.co.uk/latest-guidance/template-policies/)
NHS Mail Policy and Email Standard (https://digital.nhs.uk/nhsmail/policies)
NHS-Data Sharing Template (https://digital.nhs.uk/nhsmail/secure-email-standard)
Data Sharing Template (https://www.nhsx.nhs.uk/information-governance/guidance/data-sharing-agreement-template/?utm_source=twitter&utm_medium=social&utm_campaign=ig_staff)
A guide to good practice for digital and data-driven health technologies (https://www.gov.uk/government/publications/code-of-conduct-for-data-driven-health-and-care-technology/initial-code-of-conduct-for-data-driven-health-and-care-technology#principle-1-understand-users-their-needs-and-the-context)
Guide to Smartphones and Mobile Devices in Social Care: Providing Company Phones or ‘Bring your own’(https://www.digitalsocialcare.co.uk/social-care-technology/mobile-devices/guide-to-smartphones-and-mobile-devices-in-social-care-providing-company-phones-or-bring-your-own/)
Template Policies and Resources, Digital Social Care (https://www.digitalsocialcare.co.uk/latest-guidance/template-policies/)
Data Protection Legislation (https://ico.org.uk/for-organisations/guide-to-the-general-data-protection-regulation-gdpr/) Freedom of Information Act 2000 (https://ico.org.uk/for-organisations/guide-to-freedom-of-information/what-is-the-foi-act/)
NHS Digital: A Guide to Confidentiality in Health and Social Care (https://digital.nhs.uk/data-and-information/looking-after-information/data-security-and-information-governance/codes-of-practice-for-handling-information-in-health-and-care/a-guide-to-confidentiality-in-health-and-social-care)
Royal College of Nursing: Confidentiality (https://www.rcn.org.uk/get-help/rcn-advice/confidentiality)
Records Management Code of Practice for Health and Social Care 2016 (https://digital.nhs.uk/data-and-information/looking-after-information/data-security-and-information-governance/codes-of-practice-for-handling-information-in-health-and-care/records-management-code-of-practice-for-health-and-social-care-2016)
ICO – Video surveillance guidance (https://ico.org.uk/for-organisations/guide-to-data-protection/key-dp-themes/guidance-on-video-surveillance/)
Quality Statements
We work with people and our partners to establish and maintain safe systems of care, in which safety is managed,
monitored and assured. We ensure continuity of care, including when people move between different services.
We have a proactive and positive culture of safety based on openness and honesty, in which concerns about safety are listened to, safety events are investigated and reported thoroughly, and lessons are learned to continually identify and embed good practices.
We work with people to understand what being safe means to them as well as with our partners on the best way to achieve this. We concentrate on improving people’s lives while protecting their right to live in safety, free from bullying, harassment, abuse, discrimination, avoidable harm and neglect. We make sure we share concerns quickly and appropriately.
We detect and control potential risks in the care environment. We make sure that the equipment, facilities and technology support the delivery of safe care.
We make sure there are enough qualified, skilled and experienced people, who receive effective support, supervision and development. They work together effectively to provide safe care that meets people’s individual needs.
We assess and manage the risk of infection. We detect and control the risk of it spreading and share any concerns with appropriate agencies promptly.
We make sure that medicines and treatments are safe and meet people’s needs, capacities and preferences by enabling them to be involved in planning, including when changes happen.
We maximise the effectiveness of people’s care and treatment by assessing and reviewing their health, care, well-being and communication needs with them.
We work effectively across teams and services to support people. We make sure they only need to tell their story once by sharing their assessment of needs when they move between different services.
We tell people about their rights around consent and respect these when we deliver person-centred care and treatment.
We always treat people with kindness, empathy and compassion and we respect their privacy and dignity. We treat colleagues from other organisations with kindness and respect.
We treat people as individuals and make sure their care, support and treatment meets their needs and preferences. We take account of their strengths, abilities, aspirations, culture and unique backgrounds and protected characteristics.
We promote people’s independence, so they know their rights and have choice and control over their own care, treatment and well-being.
We make sure people are at the centre of their care and treatment choices and we decide, in partnership with them, how to respond to any relevant changes in their needs.
We understand the diverse health and care needs of people and our local communities, so care is joined-up, flexible and supports choice and continuity.
We provide appropriate, accurate and up-to-date information in formats that we tailor to individual needs.
We make it easy for people to share feedback and ideas or raise complaints about their care, treatment and support. We involve them in decisions about their care and tell them what’s changed as a result.
We support people to plan for important life changes, so they can have enough time to make informed decisions about their future, including at the end of their life.
We have a shared vision, strategy and culture. This is based on transparency, equity, equality and human rights, diversity and inclusion, engagement, and understanding challenges and the needs of people and our communities in order to meet these.
We have inclusive leaders at all levels who understand the context in which we deliver care, treatment and support and embody the culture and values of their workforce and organisation. They have the skills, knowledge, experience and credibility to lead effectively. They do so with integrity, openness and honesty.
We have clear responsibilities, roles, systems of accountability and good governance. We use these to manage and deliver good quality, sustainable care, treatment and support. We act on the best information about risk, performance and outcomes, and we share this securely with others when appropriate.
Key questions and quality statements – Care Quality Commission (https://www.cqc.org.uk/assessment/quality-statements)

Support and Care planning is something that helps you and your support staff understand what is important to you and how they should support you

Your care or support plan is where you and staff agree exactly how
people should support you and what help you need or want

You should be able to talk about what matters to you and what you want to do or achieve

You don’t have to write the care plan on your own.
You will get lots of support from whoever you decide to help you

The plan will include all the areas of your life.
• Where you need some help

• What is important to you
• What is important for staff to know so that they can help you
Knowing the important things about your life helps your staff to understand you and know what help or support you need or want.
Your care or support plan may include these things about your life:

• Your physical health

This means care and support to do with your body including washing, eating and taking care of yourself

• Your mental health

This means care and support to do so you can keep feeling well including how to support you if you get upset

• Your social needs
This means doing the things you enjoy, going out, meeting new people and being with friends or family


• Your communication needs

This is about making sure other people can understand the things you are saying

• What is important to you

Things like special friends or partners or your religion, what you like doing and what you don’t like doing

Where you live, your home

Your money and what things you need to pay for, like bills.

Getting a job or doing some training or going to college

• Your hopes and dreams

This may be wanting to go on a holiday or getting a job or some other great things

Your care and support plan should say who you want to support you
It might be that you only want either a man or a woman to support you and your care staff need to know this

Your care plan should say how you make decisions, and if you need help.
Decisions might include day to day choices and important decisions you need to make

You may want other people to help with your care plan. You might want support from:
• Your family
• Your social worker
• Your advocate
• Your doctor or nurse
• Someone else
Your support and care plan is important and will help with the following things:

Your goals and what help you need to achieve them

Helping staff to better understand:
• YOU
• What is important to you
• Your condition or disability

Keeping you well and preventing you from becoming ill

Doing the things you like to do, and trying new things when you want to

Doing things on your own and being independent

Think about what is important to you like:
• What you enjoy
• What you want to do in the future
• Your strengths
• Your needs
• Your home
• Using community facilities like shops or pubs
• If you work or volunteer, or access education, or if you would like to
• Your beliefs or values
• Any lifestyle changes that you have been thinking about. Like losing weight or exercise
• How technology could help you
• Any problems you have had getting care and support in the past
• Anything else

Remember that your support and care plan should be done with YOU and be all about you and the way you want to be supported.

It’s your life
Aroma Care People LTD, trading as Aroma Care
Company number: 09779939
Address: Dale House, The Hollow, Lutterworth, Leicestershire LE17 4BL
CQC Provider ID: 1-2218557507